
Introduction
Our recent research in Certfa Lab shows that hackers are using Google Cloud Storage (GCS) to host phishing kits and redirect users to harmful pages on other websites.
The issue has increased significantly since the beginning of 2019, and we have identified more than 100 cases of GCS targeting users of various services in the first week of May 2019. According to our investigation, this campaign is a part of a mass-distributed general phishing campaign and there is no evidence to confirm these cases are a part of a targeted attack or related to some special hacking group.
The motive and type of attacks
Weaponizing third-party services instead of hosting malicious webpages is a new trend amongst cybercriminals, and it can be described as one of the low-cost and popular techniques of cyber attack among hackers.
For example, this method allows attackers to use the website address (URL) of GSC in order to evade the anti-spam/malware systems of email service providers. In normal circumstances, the automatic defence systems of online service providers use an allow list to identify the address of legitimate services such as Dropbox, Google Drive, etc. and do not identify any sensitivity toward trusted services. As a result, the attacker can hide their malicious activities inside credible web traffic and use it to bypass these firewall of online services.
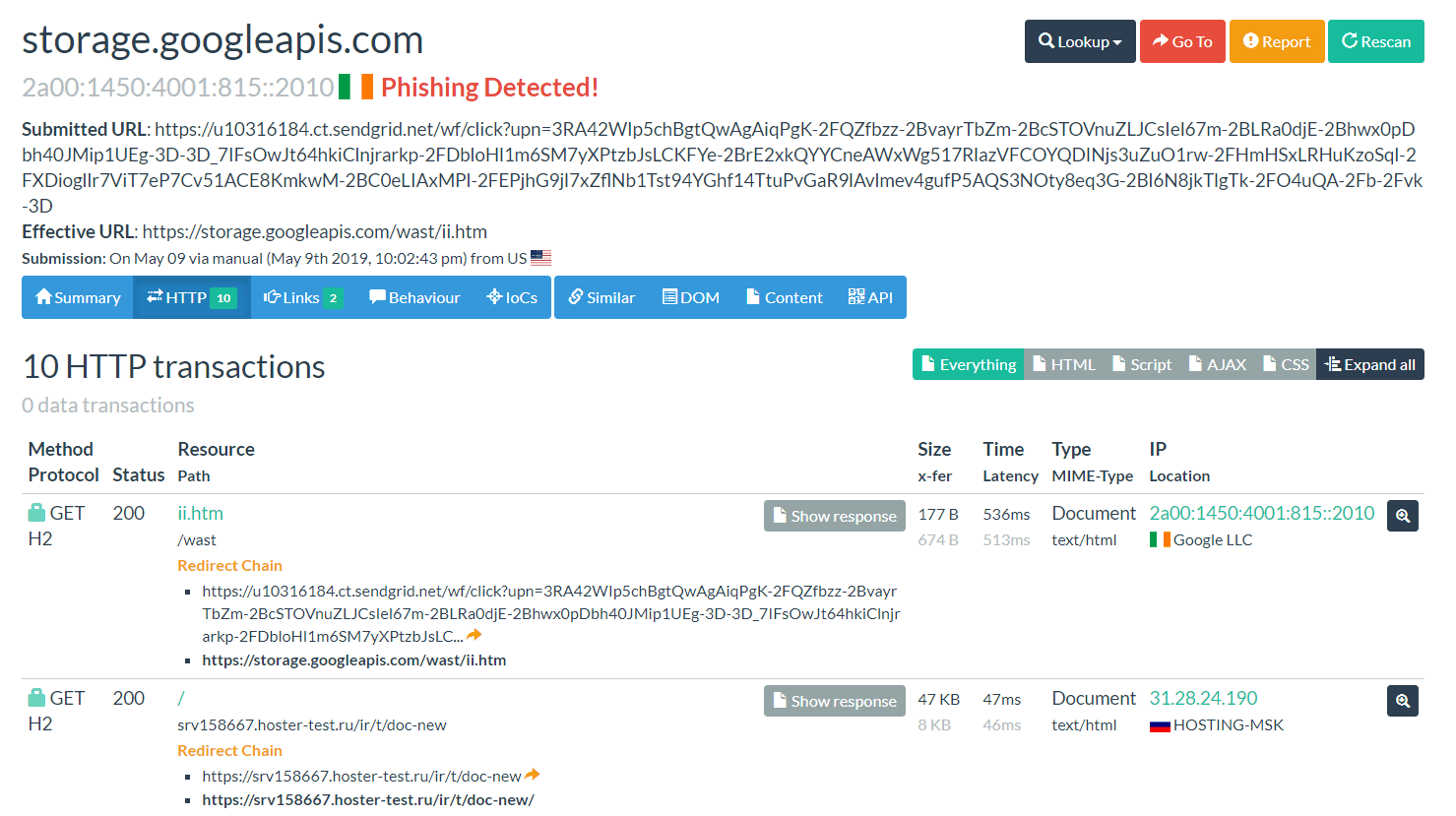
Figure 1. A submitted link on urlscan.io shows malicious links, which have been hosted on GCS and have been used as Mass-Mailing attacks.1
This technique allows attackers to send malicious links, with the phishing kit hosted on their GCS personal storage, through email or other communication methods and messaging apps. This trick allows attackers to send their targets to various phishing pages that can be used to steal different types of information and also to infect the devices of users with malware such as ransomware.
Our initial research shows that storage.googleapis.com has been exploited as a part of malicious campaigns in phishing attacks by various hackers.
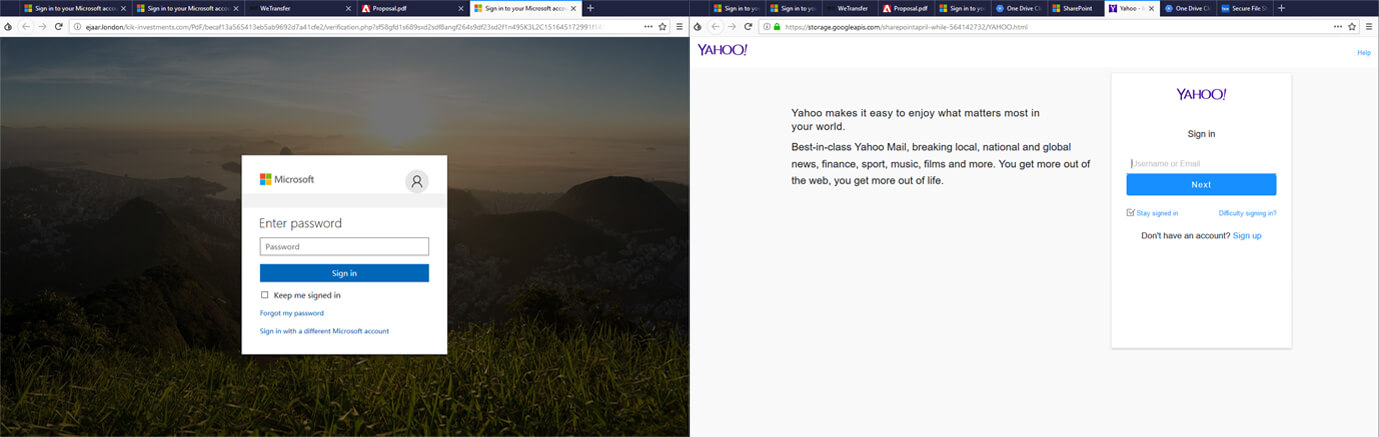
Figure 2. Samples of phishing pages that have been used in this campaign.
Although some of the phishing pages used in these attacks are relatively basic and primitive, even these pages can target users in services such as AOL, Gmail, Box, Dropbox, Yahoo!, OneDrive, Office 365, Outlook, DocuSign, and even university and bank accounts.
Common techniques of attacks
We have identified three techniques that have been used in this phishing campaign:
- Hosting phishing pages as HTML files on GCS and POST the user data to PHP files’ host servers in order to steal the targets’ information via forms.
- Hosting an initial presentation of phishing pages as HTML files on GCS, and redirect the users to the servers that host phishing kits.
- Automatically redirect the users from GCS to servers that host phishing kits.
Exploiting vulnerable servers
Using vulnerable servers and websites to host hacker phishing kits is not something new. In this phishing campaign, after hackers infiltrate vulnerable websites and servers, such as websites that use vulnerable extensions of WordPress or haven’t installed recent security patches, they upload files of their phishing kits.
Unlimited variety of phishing attacks
One of the issues that caught our attention in studying this phishing campaign, was the use of fake demos of PDF files in desktop browsers which were utilized to trick the victim and guide them to the phishing pages.
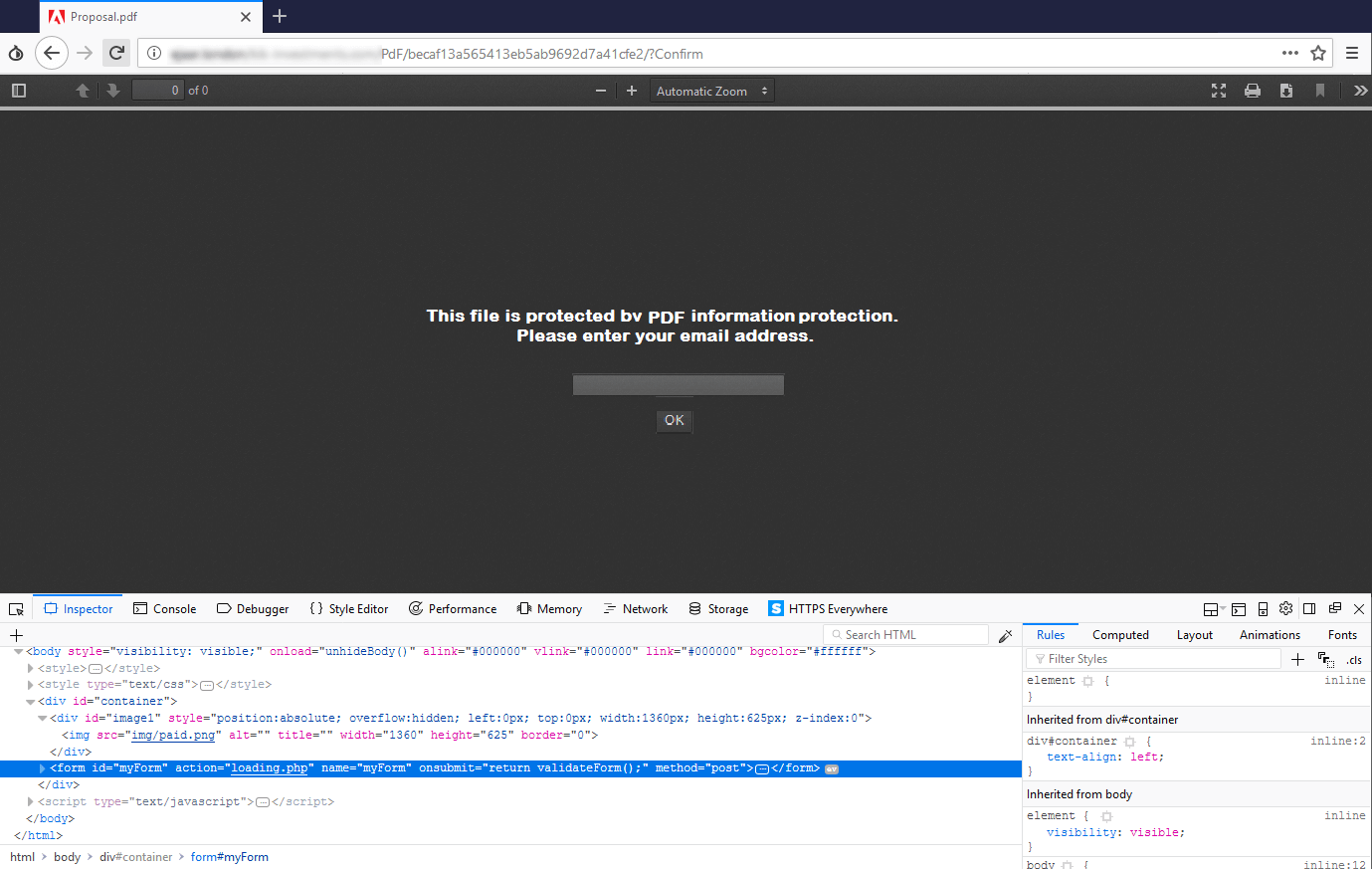
Figure 3. A sample of fake PDF file that is shown in a browser in a phishing campaign
Usually, desktop browsers can show PDF files to users directly inside the browser by using text document libraries. Relying on this fact, hackers design fake pages with similar capabilities of the browsers and claim that the fake PDF file is protected and the users must enter their email address for proof of identity. The page is designed in a way that when the user enters his/her email address, the fake login page of email is shown that gives a chance to the hackers to get credential details of the victim.
Conclusion
Using legitimate domains for hosting malicious pages in phishing campaigns has recently become very popular among cybercriminals. What we are witnessing in this campaign is hackers using Google Cloud to execute their phishing attacks.
On 5 February 2019, Proofpoint published an extensive report2 on the misuse of Github.io pages, and prior to that, Akamai had published3 details about the misuse of Google Translate service for phishing attacks.
IOCs
- 063f10972ef014e6ea39f2a387857f11d8c23cb3960f858c8af49b320e952611
- 1a1049c83578098b8f2bb81dd6d5c94899e9b3c980ef24ec37844a9fca30bc5f
- 2b1d8df255686b58f099cb2c74c5601758a4cfeccf59d84799c28151ad7048dd
- e2926a0e023e31b10ebc5664b894c821d4c25b91ad38befe9a40845df6771eb1
- storage.googleapis[.]com/accountmindspring/cashtomoalty.comtaccount.htm
- storage.googleapis[.]com/adobe-beento-846192656/adobe.html
- storage.googleapis[.]com/adropbox-glouted-350715057/index.html
- storage.googleapis[.]com/adropbox-noncontraction-936235999/index.html
- storage.googleapis[.]com/adropbox-overwound-538382774/index.html
- storage.googleapis[.]com/adropbox-revokers-25567433/index.html
- storage.googleapis[.]com/aoffice365-jabberers-450262241/index.html
- storage.googleapis[.]com/aoffice365-nondelegable-950495827/index.html
- storage.googleapis[.]com/aonedrive-inken-855408032/index.html
- storage.googleapis[.]com/aonedrive-powerset-318223121/index.html
- storage.googleapis[.]com/aonedrive-subfloor-36868329/index.html
- storage.googleapis[.]com/appjuridico/empresarial.html
- storage.googleapis[.]com/asharepoint-hillsides-276744554/index.html
- storage.googleapis[.]com/asharepoint-vivificator-798138766/001100110011hotmail.htm
- storage.googleapis[.]com/digitaldots1/redirect.html
- storage.googleapis[.]com/dlio/track/ChoiceHomeWarranty.html
- storage.googleapis[.]com/dropbox-allforyou-5556814314/index.html
- storage.googleapis[.]com/dropboxallinone-236448/index.html
- storage.googleapis[.]com/dropbox-allofus-499337129861/index.html
- storage.googleapis[.]com/dropbox-best-3734889625/index.html
- storage.googleapis[.]com/dropbox-blue-3451766797/index.html
- storage.googleapis[.]com/dropbox-eachone-147692226375/index.html
- storage.googleapis[.]com/dropbox-eachone-3972761/index.html
- storage.googleapis[.]com/dropbox-eachone83615521/index.html
- storage.googleapis[.]com/dropbox-foryou-4537381614223/index.html
- storage.googleapis[.]com/dropbox-foryou-7433695522611/index.html
- storage.googleapis[.]com/dropbox-freeforall-1614/index.html
- storage.googleapis[.]com/dropbox-mesoptery-13149/index.html
- storage.googleapis[.]com/dropbox-shareall-252744/index.html
- storage.googleapis[.]com/dropbox-shareall-348932/index.html
- storage.googleapis[.]com/dropbox-shareall-369328/index.html
- storage.googleapis[.]com/dropbox-today-641177379/index.html
- storage.googleapis[.]com/dropbox-tomorrow-751231/index.html
- storage.googleapis[.]com/eterr/ii.htm
- storage.googleapis[.]com/faceboobkvanvuyrsos/facebookonlineverfificacion.html
- storage.googleapis[.]com/facebook-account-is-blocked/facebook-verified.html
- storage.googleapis[.]com/facebookonline08052019/facebookonlinev.html
- storage.googleapis[.]com/facebook-violation-of-terms/inspection.html
- storage.googleapis[.]com/form-0/index.htm
- storage.googleapis[.]com/gphmc/mysps.html
- storage.googleapis[.]com/hotmaiil/link1.html
- storage.googleapis[.]com/iter/mre.htm
- storage.googleapis[.]com/jhoff/jsen.html
- storage.googleapis[.]com/jpmorgan1/chase.htm
- storage.googleapis[.]com/mailinbox/A-mazon.html
- storage.googleapis[.]com/mailingbox/Costco-Gift.html
- storage.googleapis[.]com/multplus/resgate.html
- storage.googleapis[.]com/navy1/navy.htm
- storage.googleapis[.]com/newdocu/dre.htm
- storage.googleapis[.]com/office-purple-82417289/index.html
- storage.googleapis[.]com/officetrue-allfree52487719/index.html
- storage.googleapis[.]com/officetrueallinone-29982817138/index.html
- storage.googleapis[.]com/officetrue-allofus-2127356/index.html
- storage.googleapis[.]com/officetrue-allofus78813995/index.html
- storage.googleapis[.]com/officetrue-blue-6133588639/index.html
- storage.googleapis[.]com/officetrue-eachone-2754433/index.html
- storage.googleapis[.]com/officetrue-foryou-17387756/index.html
- storage.googleapis[.]com/officetrue-foryou-81287569/index.html
- storage.googleapis[.]com/officetrue-osphradial-5499/index.html
- storage.googleapis[.]com/officetrue-shareall-725486/index.html
- storage.googleapis[.]com/officetruetoday-156661744/index.html
- storage.googleapis[.]com/officetrue-today-75644313769192/index.html
- storage.googleapis[.]com/officetrue-today-793369391/index.html
- storage.googleapis[.]com/onedrive-allfree-4836291/index.html
- storage.googleapis[.]com/onedrive-allfree-685379946128/index.html
- storage.googleapis[.]com/onedrive-allinone-146452/index.html
- storage.googleapis[.]com/onedrive-blue-1638517546/index.html
- storage.googleapis[.]com/onedrive-joinal-3768714983144/index.html
- storage.googleapis[.]com/onedrive-joinus-48826751/index.html
- storage.googleapis[.]com/onmsooik/index.html
- storage.googleapis[.]com/orders2quote/PO13790.pdf.htm
- storage.googleapis[.]com/proposal_order/PO13790.htm
- storage.googleapis[.]com/rikolafinh5/nwitaa.html
- storage.googleapis[.]com/schwb/schwab.htm
- storage.googleapis[.]com/schweb/red.html
- storage.googleapis[.]com/screenshortmail/earthlinkmeats.htm
- storage.googleapis[.]com/screenshortmail/materialdocumentaccount.htm
- storage.googleapis[.]com/secmsgweb/securemsg.html
- storage.googleapis[.]com/securedocs/index.html
- storage.googleapis[.]com/sharepointapril-best-7449837162/index.html
- storage.googleapis[.]com/spc-consulta-cpf/extrato-debitos.html
- storage.googleapis[.]com/spfss/prafs.html
- storage.googleapis[.]com/sreensavers/Documentaccountrackspace.com.htm
- storage.googleapis[.]com/sslwebsecuremessage/dre.htm
- storage.googleapis[.]com/ssssl/olssl.html
- storage.googleapis[.]com/suntrust/sun.htm
- storage.googleapis[.]com/tererr/dre.htm
- storage.googleapis[.]com/verficacyonitaucardfaturaonline/webcarditauonline9324g4234j.html
- storage.googleapis[.]com/wast/ii.htm
- storage.googleapis[.]com/web-sro/rastrearobjetos.html
- storage.googleapis[.]com/wordropes/footsoftprosfessionallsaolinvoice2019.htm
- storage.googleapis[.]com/xyxey/dre.htm
Footnotes:
-
Urlscan.io. Accessed May 20, 2018. https://s.certfa.com/mhYUMN ↩︎
-
Proofpoint (2019), “Threat actors abuse GitHub service to host a variety of phishing kits”. Accessed May 20, 2019. https://s.certfa.com/b89ZU5 ↩︎
-
Akamai (2019), “Phishing Attacks Against Facebook / Google via Google Translate”. Accessed 15 May 2019. http://s.certfa.com/hkhTIV ↩︎