Charming Kitten: “Can We Have A Meeting?”
Our recent investigation at Certfa Lab, the APT42 has been running multiple phishing campaigns since late 2021 and some of them are ongoing and still active.

Our recent investigation at Certfa Lab, the APT42 has been running multiple phishing campaigns since late 2021 and some of them are ongoing and still active.

During the Christmas holidays and the beginning of the new year, the Charming Kitten group, the Iranian state-backed hackers, have begun a targeted phishing campaign of espionage against different individuals to collect information.

Certfa Lab has identified a new series of phishing attacks from the Charming Kitten, the Iranian hacking group who has a close relationship with Iran’s state and Intelligence services. According to our investigation, these new attacks have targeted journalists, political and human rights activists. These phishing attacks are in line with the previous activities of the group that companies like ClearSky and Microsoft have reported in detail in September and October 2019.

Our recent research in Certfa Lab shows that hackers are using Google Cloud Storage (GCS) to host phishing kits and redirect users to harmful pages on other websites.
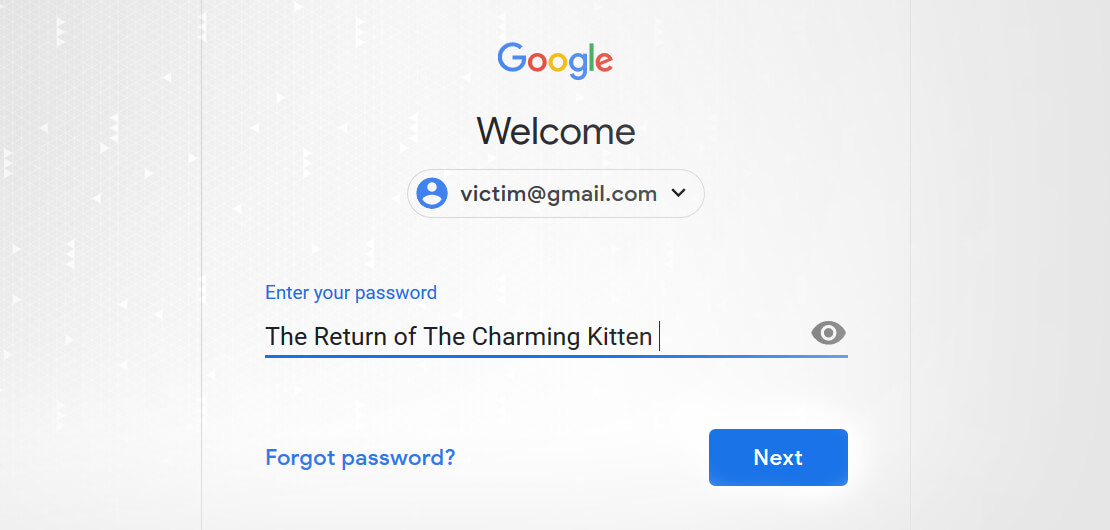
Phishing attacks are the most common form of infiltration used by Iranian state-backed hackers to gain access into accounts. Certfa reviews the latest campaign of phishing attacks that has been carried out and dubbed as “The Return of The Charming Kitten”.