
Abstract
With the increasing popularity of smartphones in Iran, these devices have turned into an attractive money-making channel for cyber criminals. This first report in a series to be published by Certfa exposes a major network of cyber criminals using malicious apps to make money by undermining Iranian users’ privacy and online security.
This report is both timely and important – so far no other organisation has offered an in-depth analysis of these criminal activities, which are costing Iranian smartphone users billions of Iranian Rials (millions of US dollars) each year.
In this report, Certfa will discuss a group of malware named PushIran.DL. The malware has in effect created a major advertising botnet that can be distributed and used in various ways to exploit users.
The misuse of third-party services in order to send notifications, manipulate other programs and deceive users are only some of the activities carried out by the creators of these malware, who pose a serious threat to the privacy and digital security of millions of smartphone users in Iran.
The PushIran.DL malware, which is currently only operational for the purposes of profiteering, are largely detected by reliable anti-virus software such as Kaspersky, ESET NOD32, Avira, Dr.Web, and Trend Micro. Users at risk may use this software to ensure that their devices are not infected.
Introduction
The development of downloadable malware and adware has became a prominent activity in mobile apps and internet advertisement markets. These criminal acts have increased the prevalence of smartphone infections and if not seriously confronted, we expect to encounter more far-reaching and dangerous threats in the not-too-distant future.
The malwares that are the subject of this report have been grouped under the title ‘PushIran.DL’. This is a family of fake and destructive Android apps which are distributed across Iran’s mobile network — whether through Telegram Messenger or other Android malware — by playing different tricks, including distributing downloaders and adult apps, and by sending text messages and deceptive notification ads in other mobile apps. Their creators are constantly developing new versions and releasing further infected files.
No accurate data about the full extent of infection of mobile devices by PushIran.DL is available, but we believe that more than 10 million Android devices in Iran have been infected. The documents collected from just one of the attackers’ Control and Command (C&C) servers 1 revealed that approximately 1,369,000 Android devices have been infected.
This research has revealed to us is that the PushIran.DL malware family has developed vast Android-based infrastructure to support a giant botnet of spam and mobile adware in Iran.
Anti-virus tools categorise the infected malwares that we define as part of the PushIran.DL family under titles such as: 3
- TrojanSMS.Agent
- Android.Hiddad.GEN
- Adware.Adpush
- Android.HiddenApp.GEN
- FakeAntiVirus
- Fakealert
Currently, the PushIran.DL malware performs the fuction of the creation of a user base and the formation of a mobile botnet for commercial uses. The main activity consists of stealing Android device information and recording users’ credential details via push notification services. The developers of these malwares have used this data for advertisement but in the near future, it is very possible that they will use it for more destructive purposes, such as the implementation of phishing attacks, the release of ransomware and as cryptocurrency extractors.
Origins of PushIran.DL
According to our investigations and existing evidence, the companies “Pouya Ertebat Raman (Raman) 4” and “Raazgostaran Andisheh Fartak (Raaz) 5” are the two main developers and spreaders of PushIran.DL in Iran.
Raman: Pouya Ertebat Raman is a company which produces mobile apps, sells the source code of software, and produces online advertising. It was registered by Mohammad Hossein Karbalaei Sadegh, Mohammad Naftchi Langeroudi and Seyed Hamid Mousavi Khoshdel on 17 July 2017 (26 Tir 1396). 6
Raaz: Raazgostaran Andisheh Fartak is a company active in IT and communications, consulting, marketing and internet advertising. It was registered by Razieh Hemmati Goshtasb, Hamideh Hemmati Goshtasb, Soghra Dizgani and Payam Zamharir. The company officially started to operate on 28 May 2017 (7 Khordad 1396). 7
The Main Actors
After analysing captured information from the recognised malware and a two month phase of monitoring communications among malwares, developers concluded that a number of individuals and firms are involved in spreading the PushIran.DL malware.
In the following reports we will discuss these entities in detail, but according to the evidence that we captured from digital footprints, some of the main distributors of these malware include Mohammad Hossein Karbalaei Sadegh (nicknamed “Omid” and “Omidmhks”), Ali Motamedi and Milad Faraji. The function of some of the released files will be mentioned later in this report.
What is remarkable about PushIran.DL is that its creators have created and launched the infected apps using the nicknames of the owners (those who work in Pouya Ertebat Raman), customers and other co-workers of the company. Via the attacker’s C&C servers, we were able to find a list of names that related to Raman:
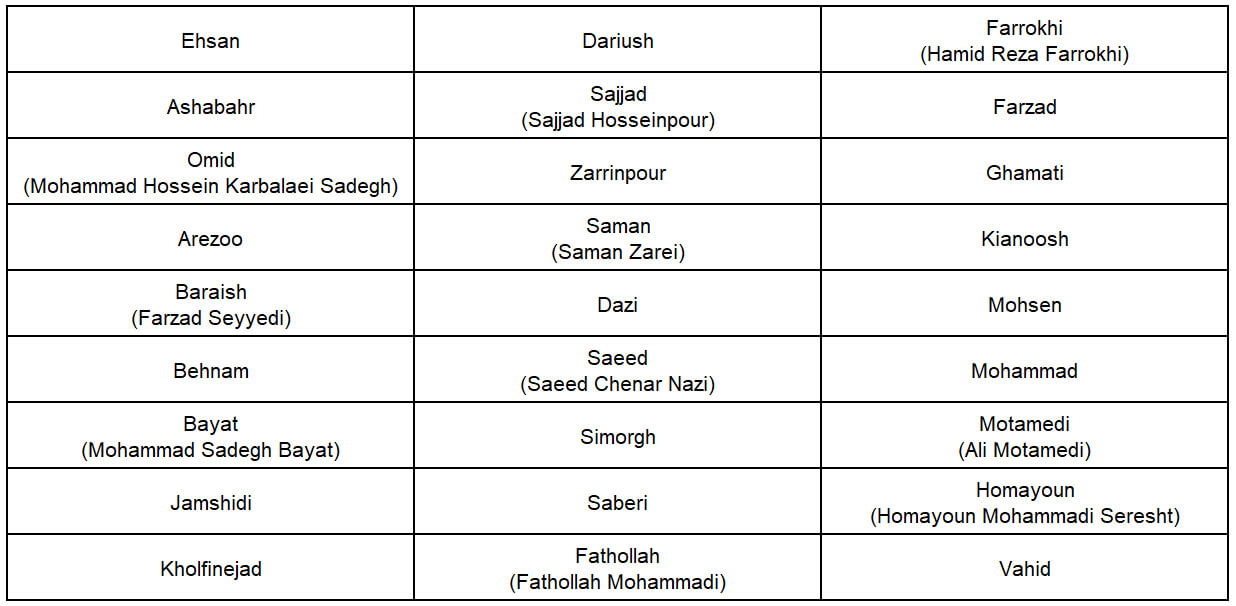
Table 1. A list of individuals who are related to Raman and developed malware under Pushran.DL campaign.
We were also able to identify some of the developers of this malware in Android app stores. For instance, Mohammad Hossein Karbalaei Sadegh (Dima), Farzad Seyedi (Baraish Team), and Ali Motamedi (Tosewe-ye-Paydar) are some of the PushIran.DL developers who have intentionally released infected Android apps on CafeBazaar.ir (the Iranian version of Google Play) and other Iranian Android app stores. [^7] [^7]: Cafe Bazaar, “ضد ویروس”. Accessed July 30, 2018. https://s.certfa.com/KztV5g
Cafe Bazaar, “Samaanak Smart Keyboard”. Accessed July 30, 2018. https://s.certfa.com/XUEBV5
Cafe Bazaar, “زودشارژ (شارژ سریع باطری)”. Accessed July 30, 2018. https://s.certfa.com/WmBm4e
Cafe Bazaar, “Advanced Antivirus”. Accessed July 30, 2018. https://s.certfa.com/PmLD8X
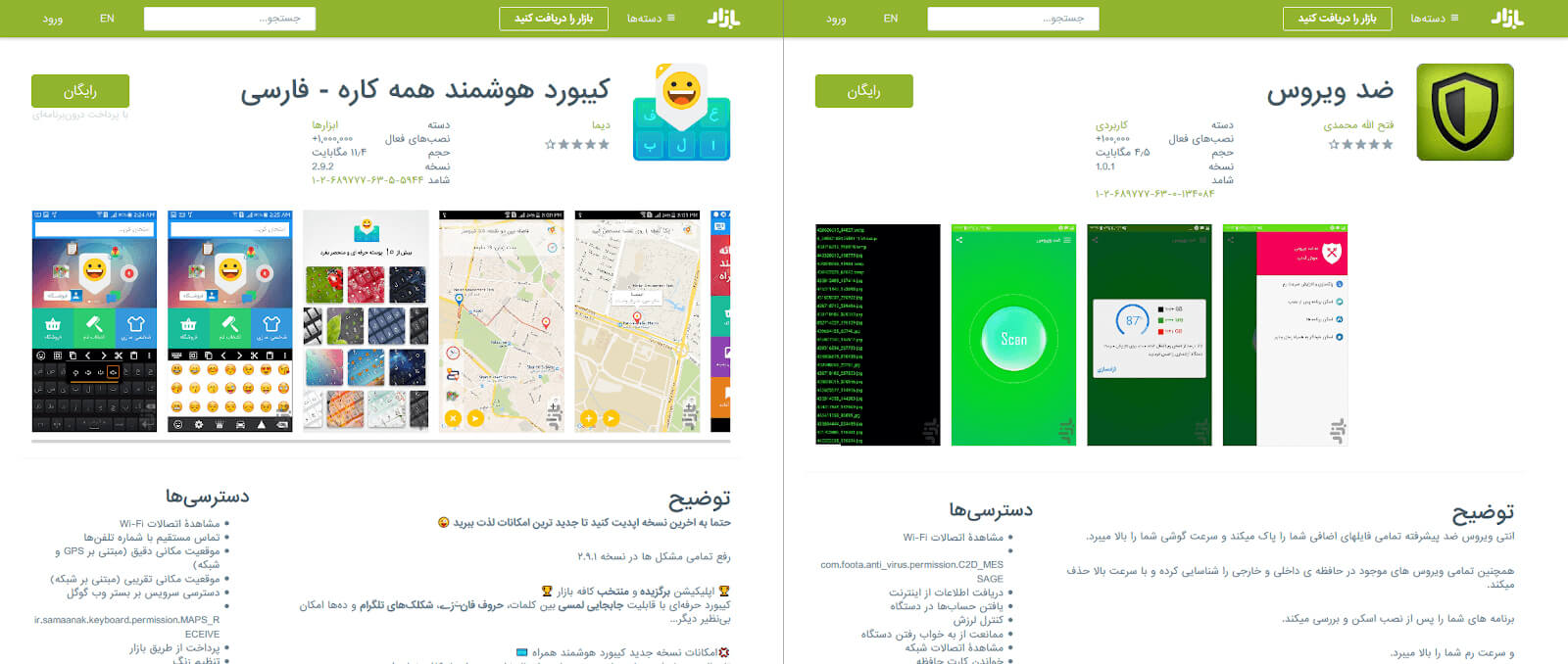
Figure 1. Samples of apps and PushIran.DL related developers (‘All Purpose Smart Keyboard’ with more than 1 million installations and an anti-virus with more than 100,000 active installations.)
Aria Tosewe [^8], who has previously used the name Ali Motamedi [^9], is another of the individuals who has released infected applications on Google Play. Some of the users who installed Motamedi’s app have complained about annoying ads forcing them to download other apps without their consent and navigating users to other websites.
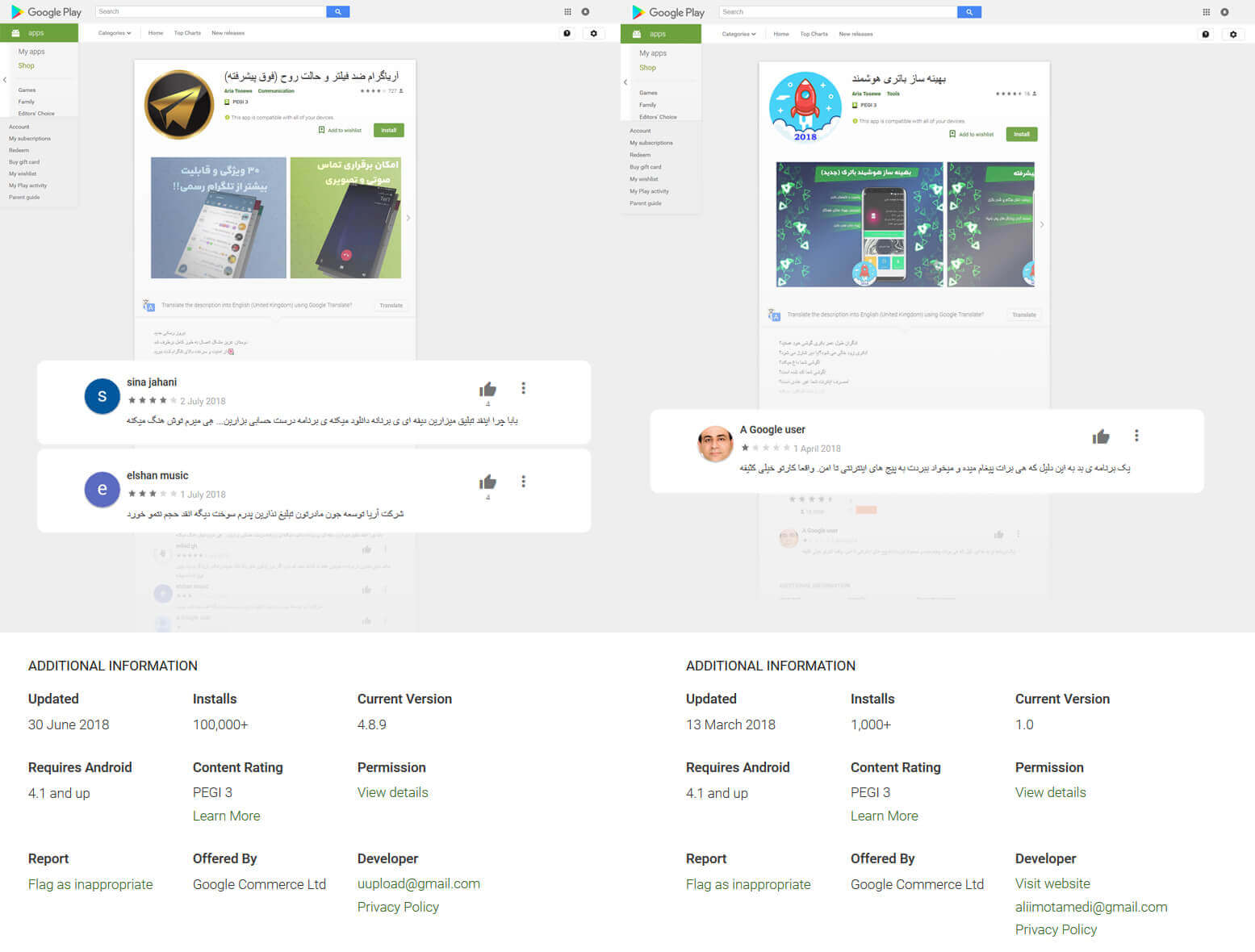
Figure 2. Comments from users about Ali Motamedi’s apps on Google Play 8
Analysis
As of August 2018, we have been able to collect 220 samples of PushIran.DL. The examples we have collected appear to share a number of common features. Nevertheless, we believe that there are far more infected apps out there than those we have detected. Yet based on the activities of these malicious apps, we can assert that the main culprits have been identified.
Names of Suspicious and Malicious Apps
The title of the files that have been released by 1 July 2018 are as follows:
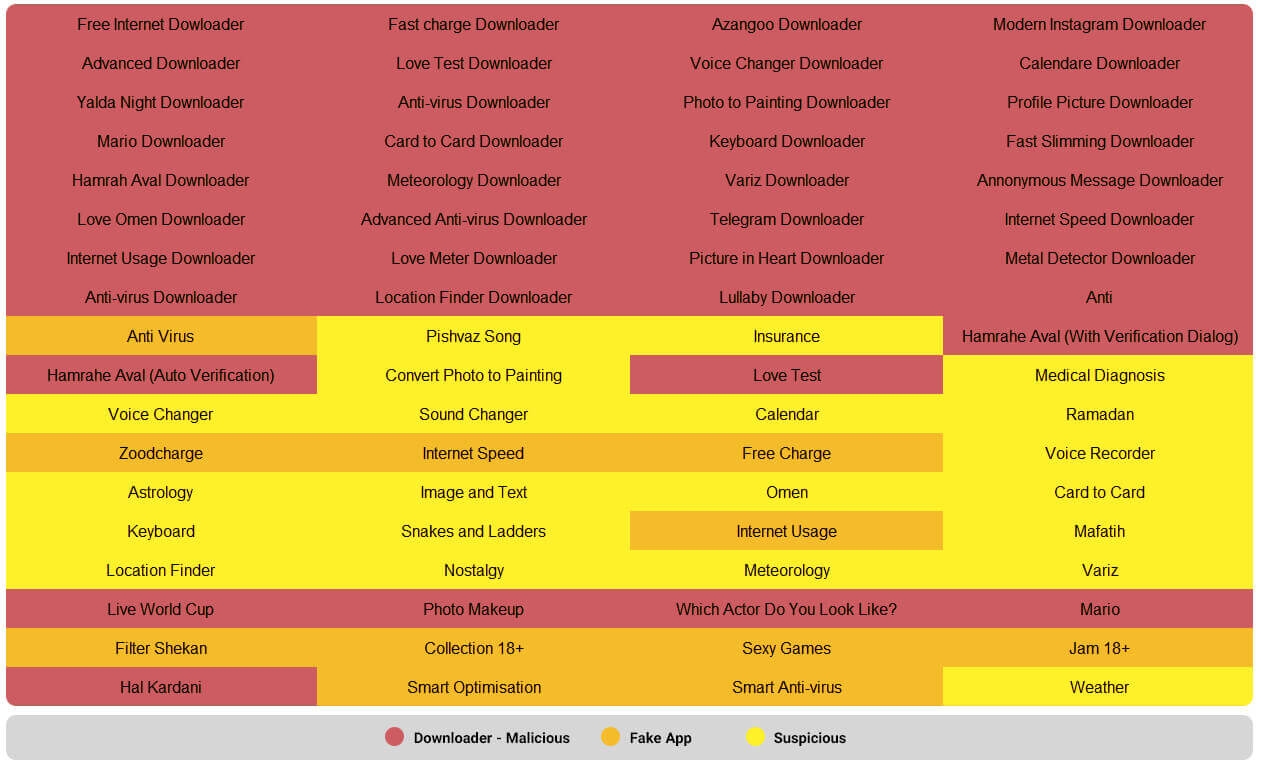
Table 2. A list of suspicious and malicious apps that have been released by 1 July 2018. 9
### Value-Added Services
According to our assessments, some of the PushIran.DL apps inflict different costs upon users by activating Telecommunication Value-Added Services (VAS).
After entering into agreements with their customers (companies and VAS providers), the developers of PushIran.DL add the activation of text message VAS services to their apps as one of their destructive capabilities. According to the agreements, the attackers receive a small amount of money from their customers as commission.
Our observations show this has been done both involuntarily (without informing the users and getting their consent) and voluntarily (through false and deceptive advertising plans). It causes financial losses to the user as on average users’ credit reduces at a daily amount of 2,000 to 4,000 IRR (0.04 to 0.09 USD), or charges similar amounts on their periodic bills.
Based on collected data from one of the malware servers, companies that have agreements with telecommunication companies receive an approximate sum of 1.17 billion IRR (25,570 USD) through VASs from only 10 malicious apps. The names of the 10 infected apps with their corresponding daily installation rate and average daily revenue are listed below:
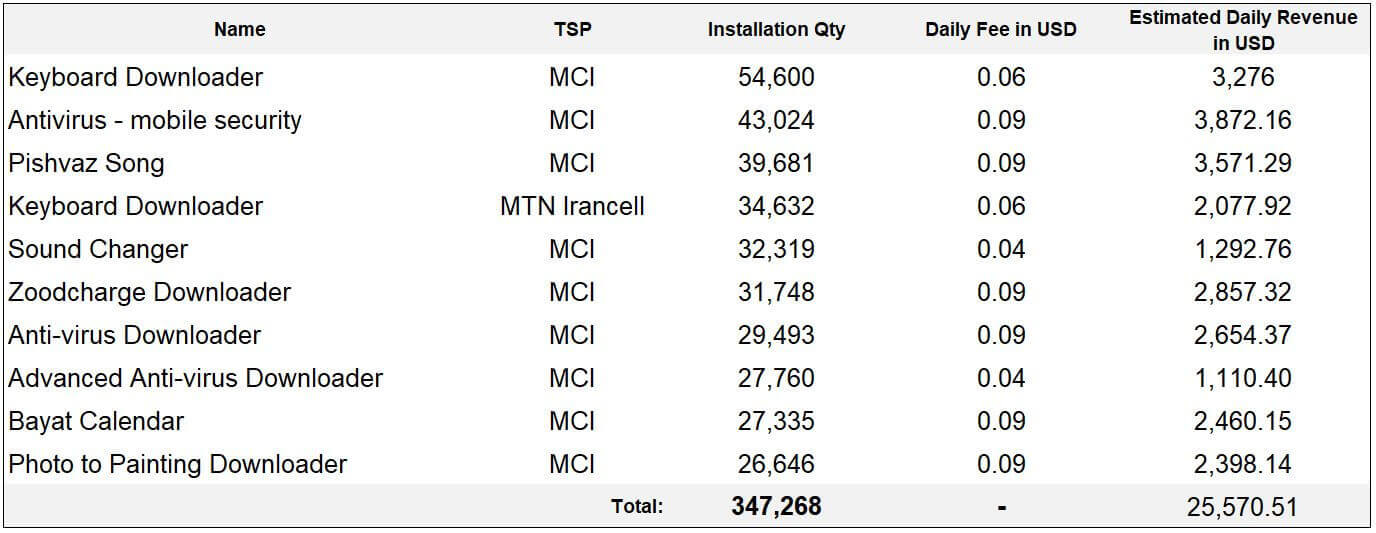
Table 3. A list of PushIran.DL apps with estimated revenue 10
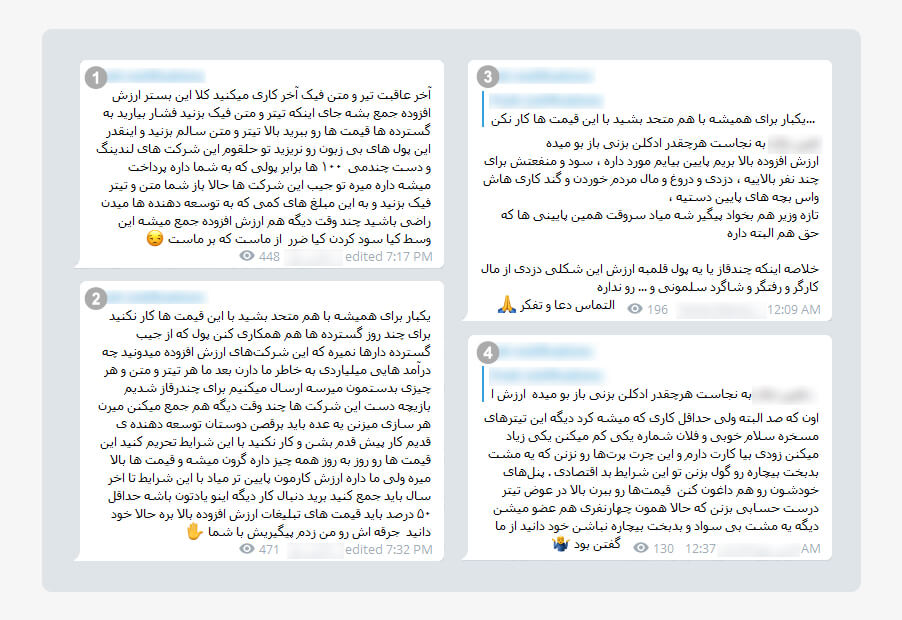
Figure 3. PushIran.DL malware developers’ dissatisfaction with low level of income of working with VAS companies
1- The final result of using false titles and texts will be to finally terminate this whole business of value added services. Instead of fake titles and contacts you should press against these Gosterdeh-ha, raise the prices and put real titles and texts and don’t throw this wandering money in the pockets of these [VAS] and multiple-handed companies. The money that goes in their pockets is 100 times your income, and then you keep putting fake titles and contents and accept the little sums that they give to developers. Soon VASs will be eliminated, and who will have gained and who will have lost? You reap what you sow!
2- Once and for all unite with each other and don’t work with these prices. For a couple of days Gosterdeh-ha should also cooperate. No money is spent from their pocket is it? Did you know that these value-added companies make billions of Tomans from what we do? And then, we post every title and text that comes to our minds for peanuts. We have really been played by these companies and soon they will all go and leave us. We are dancing to their tune. Old developers should step forward first and boycott these companies. Prices are going up every day and the value of our work is being reduced by that. If this goes on, by the end of the [Iranian] year you should all be looking for jobs. Remember this! The advertising price for value-added products needs to go up by at least 50 percent [for this to become profitable]. I sparked the conversation, but it’s your choice. You should decide.
3- No matter how much perfume you put on filth, it still stinks. No matter what we do, there are some issues with the value-added business. The profits and gains are for those few on top, and stealing and lying is a murky business. And then if the [ICT] Minister decides to prosecute, he’ll come straight to us, and he’ll be correct! In sum, whether it is a good amount of money or just peanuts, it isn’t worth stealing from workers, street sweepers and barbers. I beg that you pray and think!
4- That is 100 percent true but the least that we can do is that we don’t put these ridiculous titles such as hey how are you and this number will decrease one and increase one and hey come over here I wanna talk with you etc, so that in this harsh economic situation a bunch of poor people and toilers wouldn’t be deceived. They should destroy their own panels and raise their prices and instead use real titles so that if only a couple of people become members, they are not illiterate and poor. I had to say it and it’s your choice to listen!
### The Scope of Activity
The activity of PushIran.DL is extensive. Some of their current activities are listed below:
- Guaranteed installation of Android apps (Hidden downloads and involuntary display of new apps for download)
- Sending notifications based on operator, location, age group, gender and user’s device model
- Increasing Instagram and Telegram post views
- Displaying commercial pop-ups
- Clickjacking for increasing number of views of different websites
- Directing users to various web pages, such as VAS websites
In Figure 4, some advertising messages sent by PushIran.DL developers can be seen. These messages have been sent for marketing purposes. The number of targeted users is between 1.5 and 12 million. The use of malware has been mentioned in this screenshot.
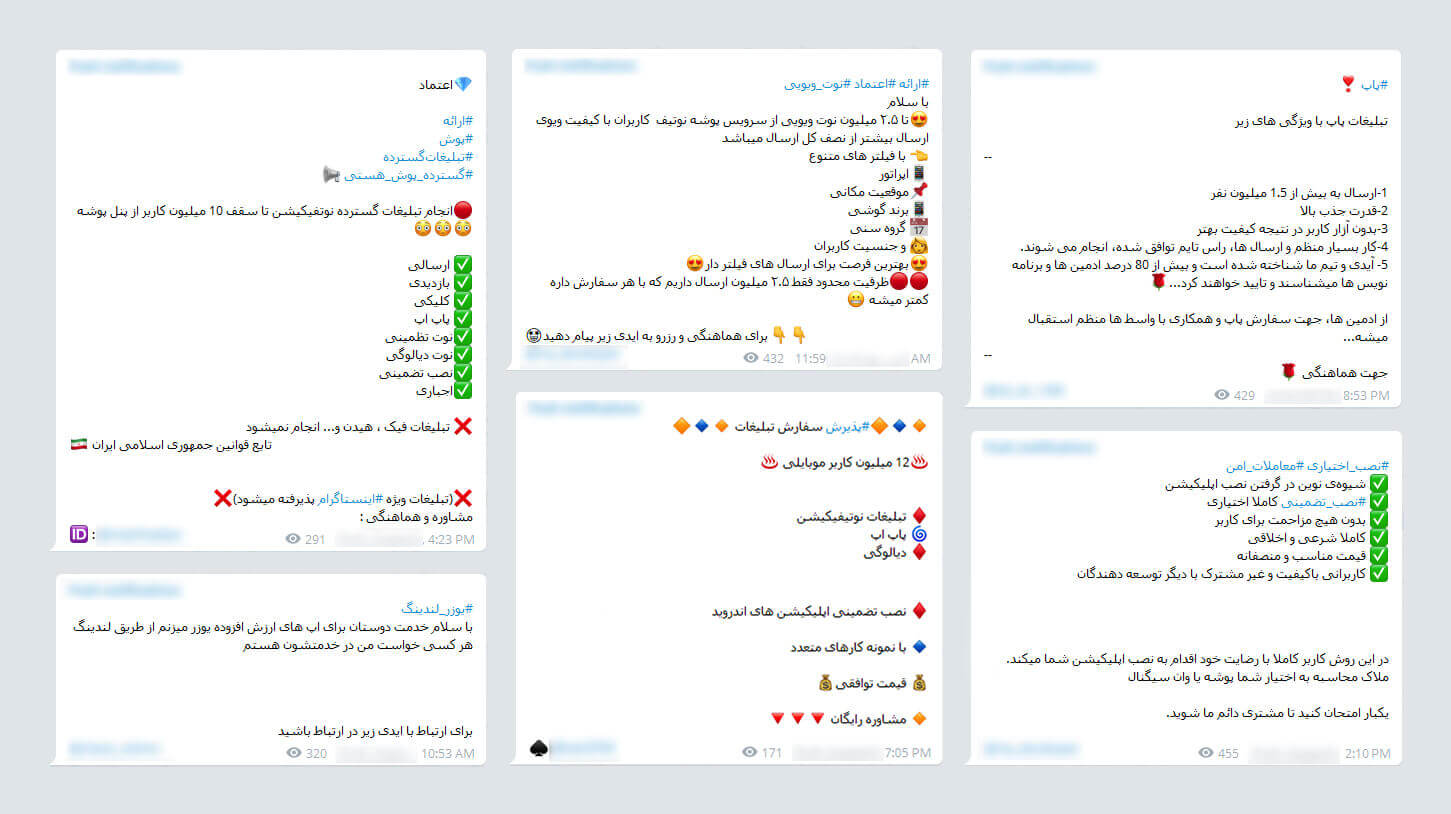
Figure 4. Some of the messages exchanged among PushIran.DL related individuals for marketing. These messages contain notes about the technical and functional capabilities of their malware.
- 12 million mobile users
- Notification ads
- Pop-up
- Guaranteed installation Android apps
- With a variety of samples
- Negotiable price
- Free consultation
- Greetings
- Up to 2.5 million views by [using] push notification services. More than half of sent notification will be viewed.
- With various filters
- Operator
- Location
- Cell phone brand
- Age group
- And users gender
- Best opportunity for sending targeted ads.
- For coordination and reservation send a message to the ID below
- Extensive notification advertising up to 10 million users from Pushe.co [by]:
- Sending
- Viewing
- Clicking
- Pop-up
- Guaranteed notification
- Dialog notification
- Guaranteed installation
- Mandatory
- No hidden or fake advertisements
- In accordance with the laws of the Islamic Republic of Iran
- We accept special Instagram advertising [as well].
Disguised Apps and Third Parties
It is noteworthy that most developers responsible for distributing PushIran.DL release applications with generic titles such as “Persian Keyboard”, “Antivirus”, “Device and Battery Optimizer”, “Augury and Horoscopes”, “Weather Forecast”, “Religious Prayer”, “Persian Calendar”, many of which have similar user interfaces and functionalities. These similarities could derive from the use of identical source codes, some of which are available ‘off-the-rack’ from websites and Telegram channels.
These developers, alongside the companies and groups mentioned in this report, have created a medium for the sale of push notification management panels and the granting of concessions within apps that are available on app stores. What they have created can be described as a ‘black market’ of mobile apps being used for advertising purposes.
The consequences for the users of these apps—which are publicly available on app stores—should be a matter of serious concern. The administration and management of these apps has been transferred to third parties, whose interest in buying mobile apps with massive user bases lies in profiteering, with little regard paid to the consent of app users. In other words, commercial and administrative access to these apps is being sold secretly, without respecting the privacy of users, nor the regulations of app stores such as Cafe Bazaar or Google Play.
In the posts of the Telegram channel of the managers of Pouya Ertebat Raman, we encountered such cases:
“The full concession of a chosen app in Cafe Bazaar with access to OneSignal admin panel and the data of 19,700 users (active installations) will be sold at 200 million IRR (4,545 USD)”.
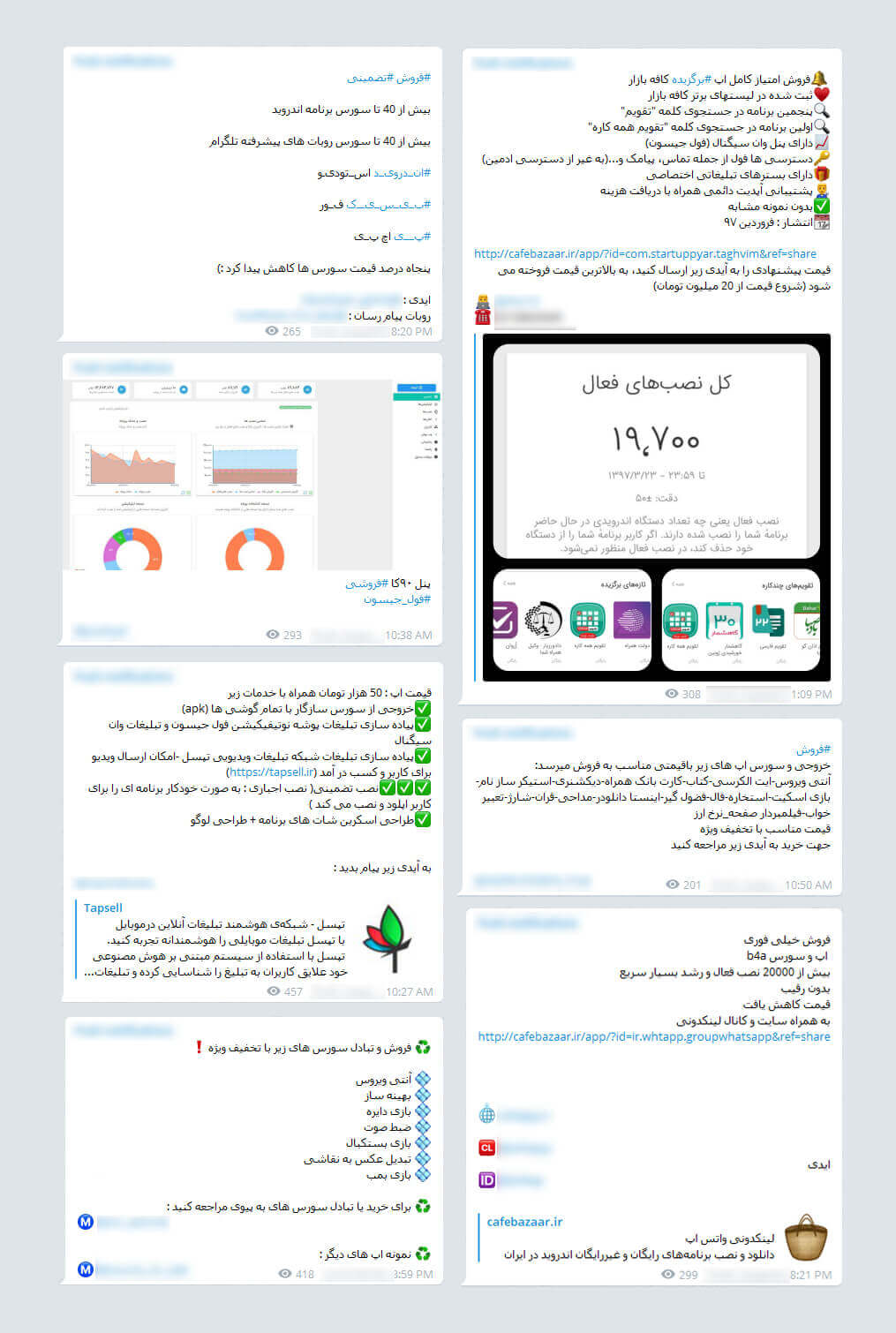
Figure 5. Some samples of posts about the sale of source codes and the transfer of user panels for sending notifications (Source: Telegram channels belonging to PushIran.DL developers).
The Analysis of the PushIran.DL family
1) PushIran.DL downloader
Technical evaluation of samples of PushIran.DL malware indicates that after infecting Android devices, downloader files make contact with C&C servers. This will serve the purpose of recording devices’ primary data (such as the model, the telecommunication service provider, location, etc.).
Afterwards, the attacker controls the malware remotely by sending different commands through push notifications such as ads, various app download links and directing users to other websites.
Some of these downloaders, by default, start receiving suspicious new APK files from the internet immediately, after primary running through calling link of file, which have been installed in downloader codes by default.
Attackers use two methods for distributing suspicious APK apps, that may be more powerful and destructive malware:
- Private Servers: By using private servers, attackers are able to easily replace uninfected files with infected ones. For example dl2learnasan.ir has been used for this purpose.
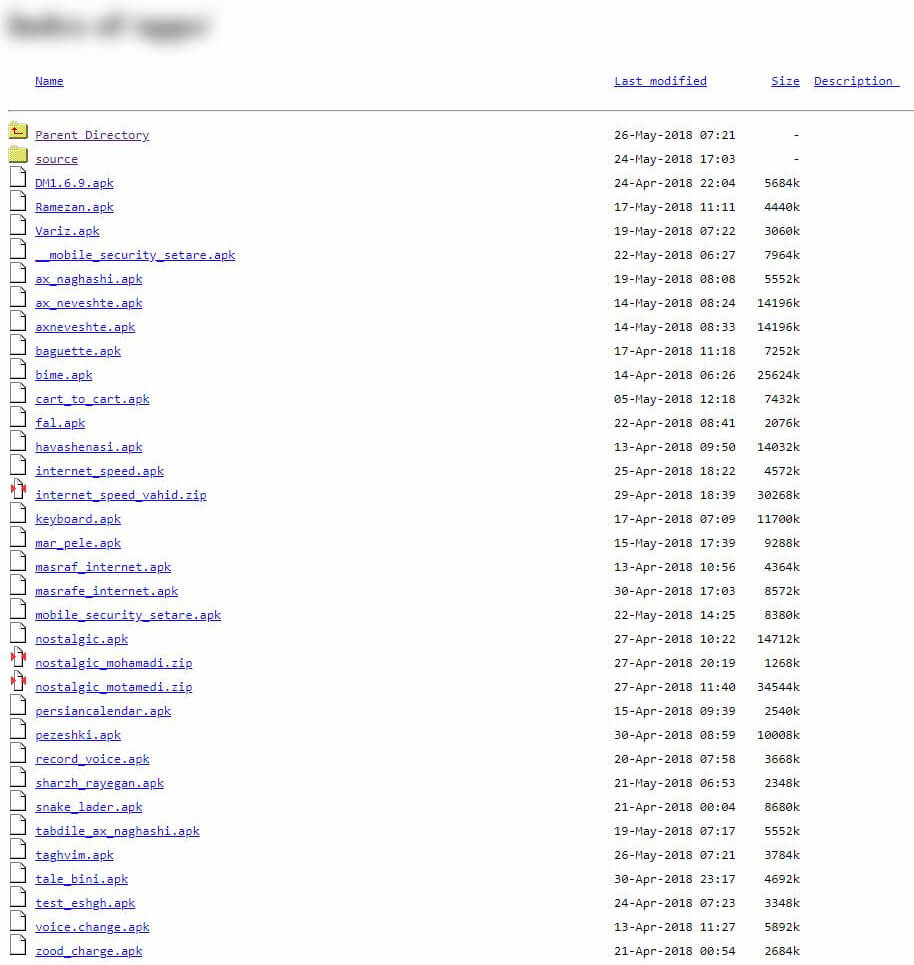
Figure 6. List of files, accessible on dl2learnasan.ir server
- File Sharing Servers: Sometimes, attackers use file sharing servers to hide their traces, accelerate the distribution of files and store the exact number of downloads to their customers, who had ordered ads. An example is the uupload.ir service, through which massive infected files were shared in Spring 2018.
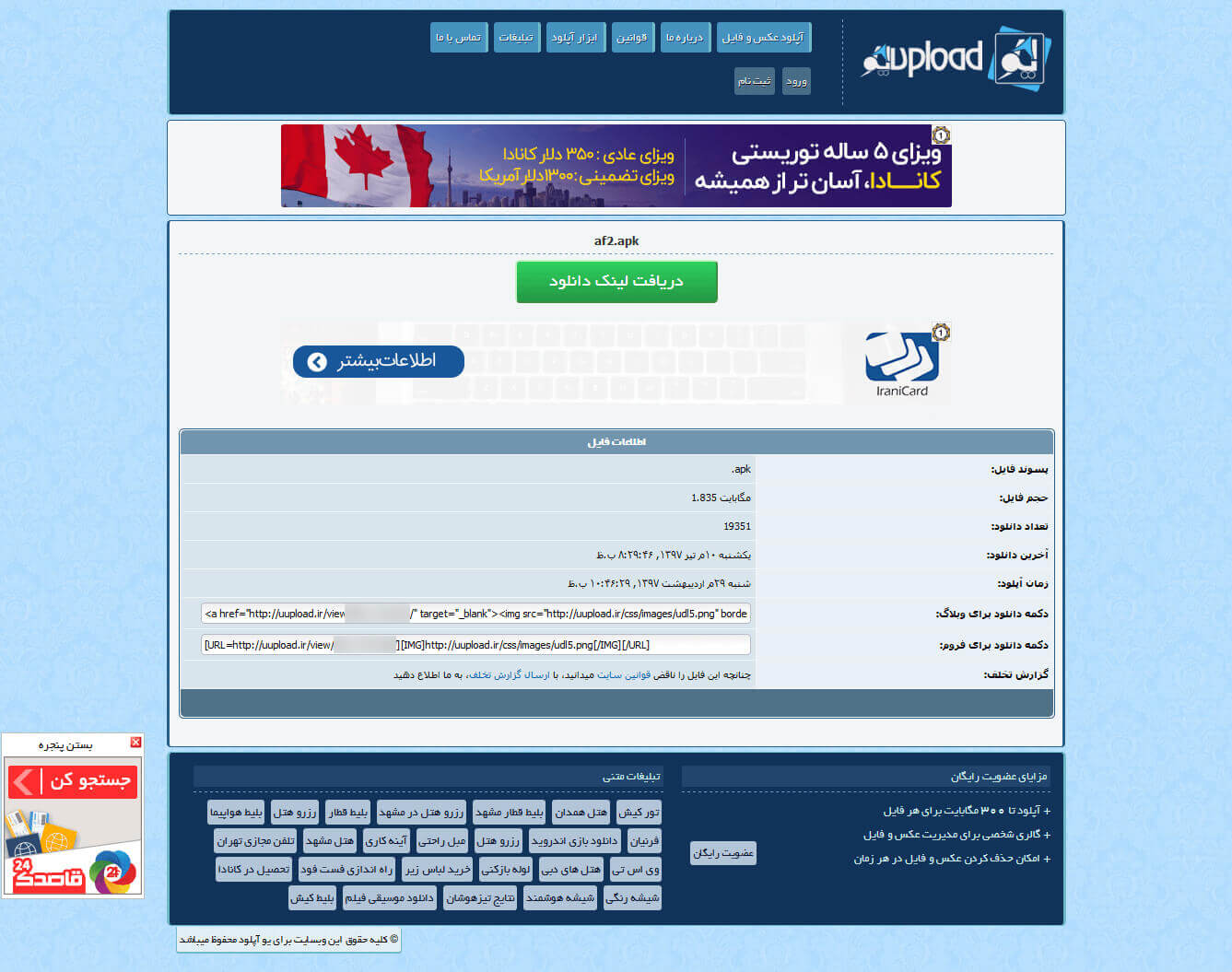
Figure 7. A sample of downloader files, uploaded on uupload.ir with more than 19,000 downloads.
Figure 8 illustrates the function of these downloaders (for example, based on function of com.newdownloader.antivirus_mohammad and ir.pushiran.hamrahdownloader5 downloaders).
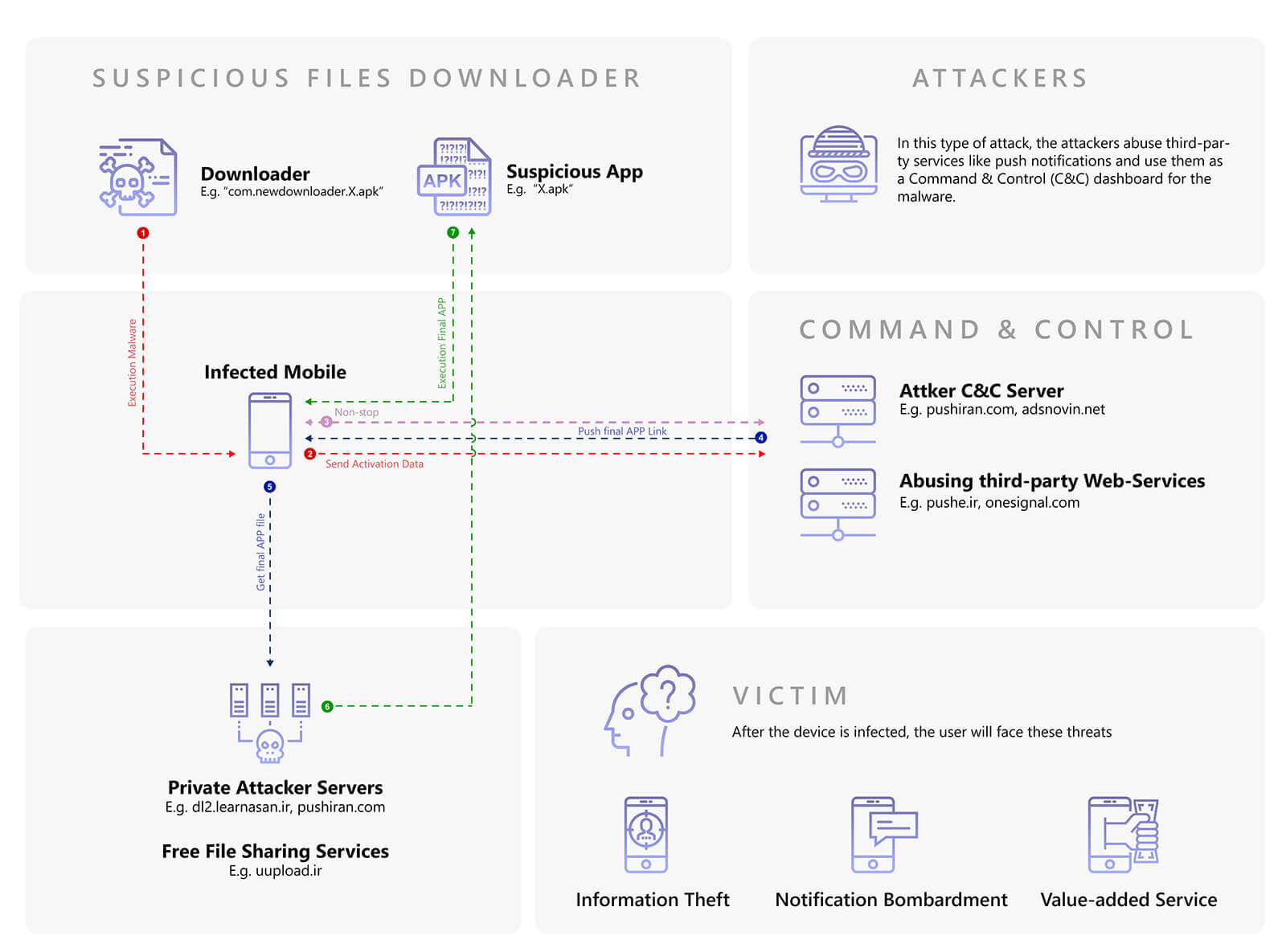
Figure 8. PushIran.DL downloaders’ mechanism
### 2) PushIran.DL store downloaders During our evaluation of PushIran.DL files, we encountered downloaders which were distributed mainly with the aim of increasing the number of users of apps that are available on Android stores.
Since some of Android app stores (such as Cafe Bazaar) calculate the demonstrated statistics of “number of installations” based on a count of the number of installed apps on users devices, This method of selecting popularity of the apps, allows malware developers to manipulate the system and artificially inflate the number of downloads.
For example, the developer can send a command and ask the malicious app to start downloading another app. When an app starts to be downloaded by tens of thousands of users, the new malicious app might appear in the ‘Trending’ section of the app store, and other users whose devices are not infected with PushIran.DL may become affected by it. This cycle can be perpetuated to spread malware to large user populations.
Besides this, these downloaders—similar to all PushIran.DL files—registered users’ device information such as IMEI, TSP, and DeviceToken (among others) on their push notification service.
Figure 9 is a summarised demonstration of the mechanisms of these downloaders (for example based on function of ir.gotoup.flashlight and com.newdownloader.ax_naghashi_zz_homayoun).
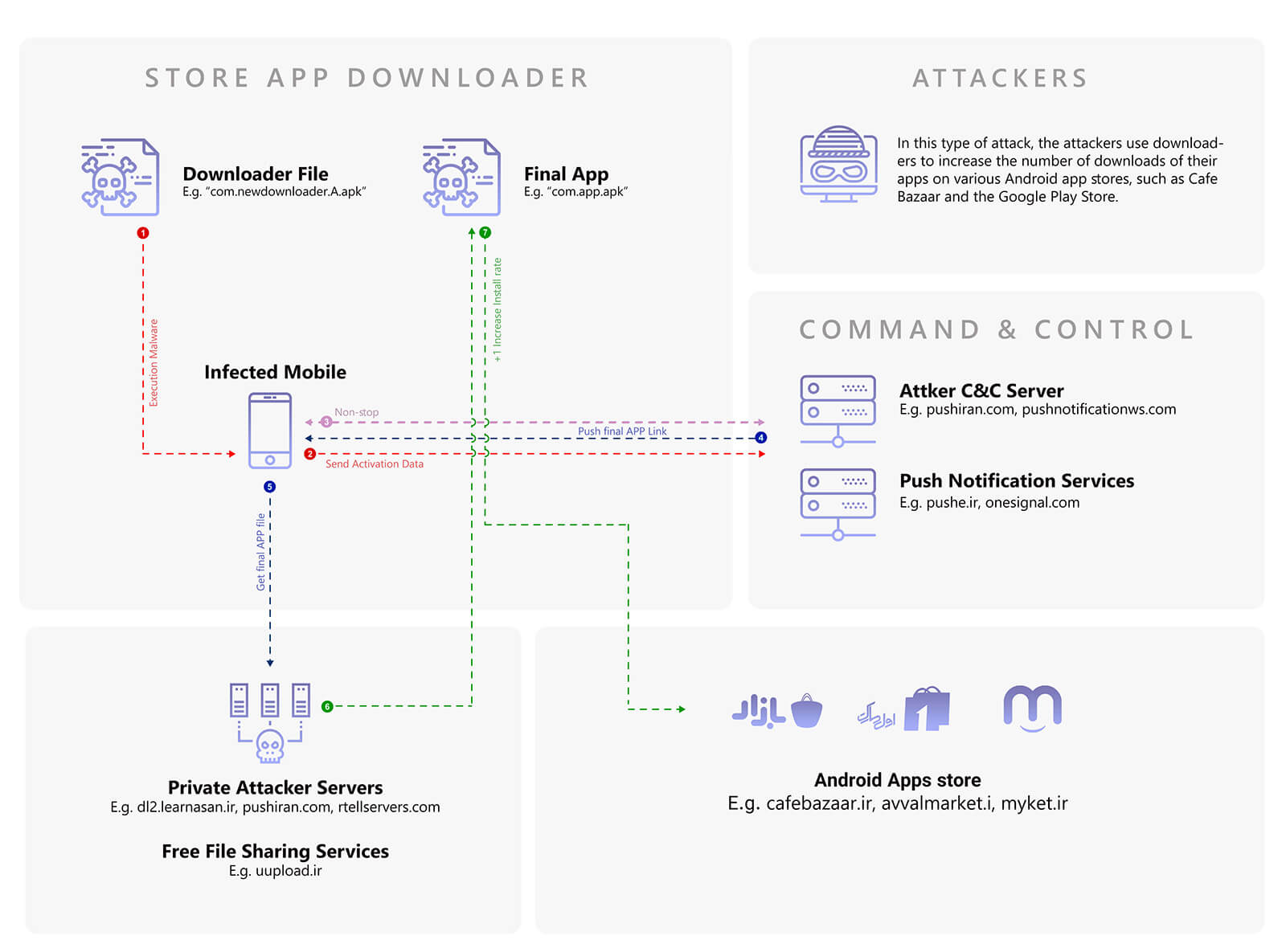
Figure 9. PushIran.DL store downloaders’ mechanism
### 3) PushIran.DL Metadownloaders
Another type of PushIran.DL file are ‘meta-downloaders’, which are downloaders that add new downloaders to users’ devices after infecting them. These metadownloaders enable attackers to install newer and more diverse types of malware.
After various assessments, we can assert that so far the main purpose of the distribution of this type of file has been merely to create larger user bases for push notification services, which can be used specifically by attackers for sending ads.
Figure 10 is a summarised demonstration of the mechanisms of these metadownloaders (for example based on function of com.bestmaker.antipackage and com.blod.taghziye).
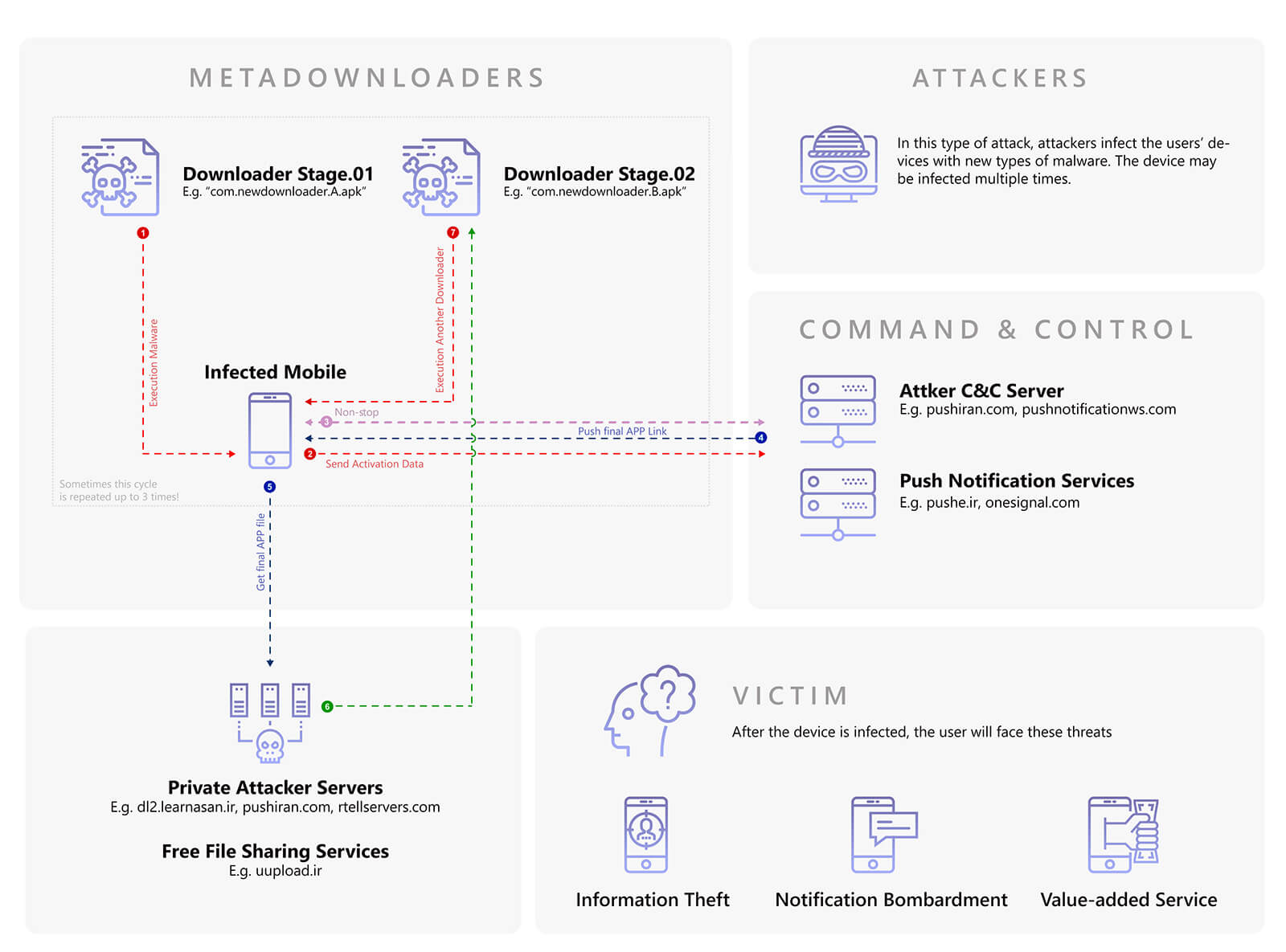
Figure 10. PushIran.DL Metadownloaders’ mechanism
### 4) Irrelevant notifications
A noteworthy issue about PushIran.DL is the notifications that have no relevance to function of apps. Some samples of this type of notifications are shown in Figure 11.
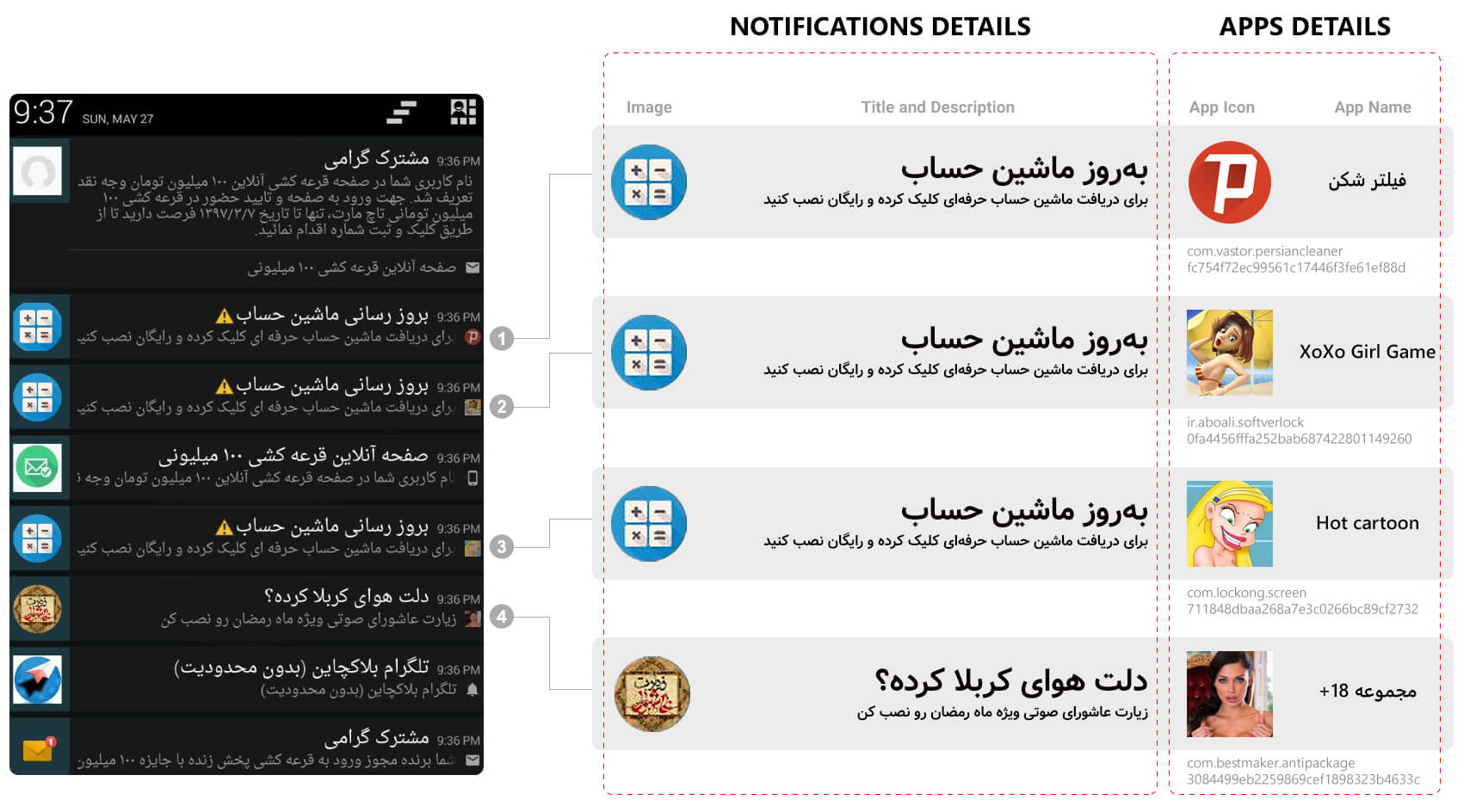
Figure 11. Notifications which are irrelevant to function of the advertised software
- Case 1: A fake app with the Psiphon icon and title “circumvention” sent a notification titled “calculator update” to the user in which the “free download of a calculator app” has been mentioned.
- Case 2 & 3: Similar to the Psiphon app, two apps “XoXo Girl Game” and “Hot Cartoon” have sent similar ads to the user.
- Case 4: Fake app “18+ collection” has sent a notification “Are you eager to go to Karbala?” to users in which the download and installation of “an audio Ziyarat Ashura for Ramadan” has been mentioned. 11
5) Dialog Notifications
Another type of annoying notification shown by PushIran.DL apps are pop-ups, whose related data have been sent to users devices thorough push notifications. Pop-ups appear on users’ devices main screens as advertising dialogues. Users are not aware of the source of these notifications. Two samples of these ads are shown in Figure 12.
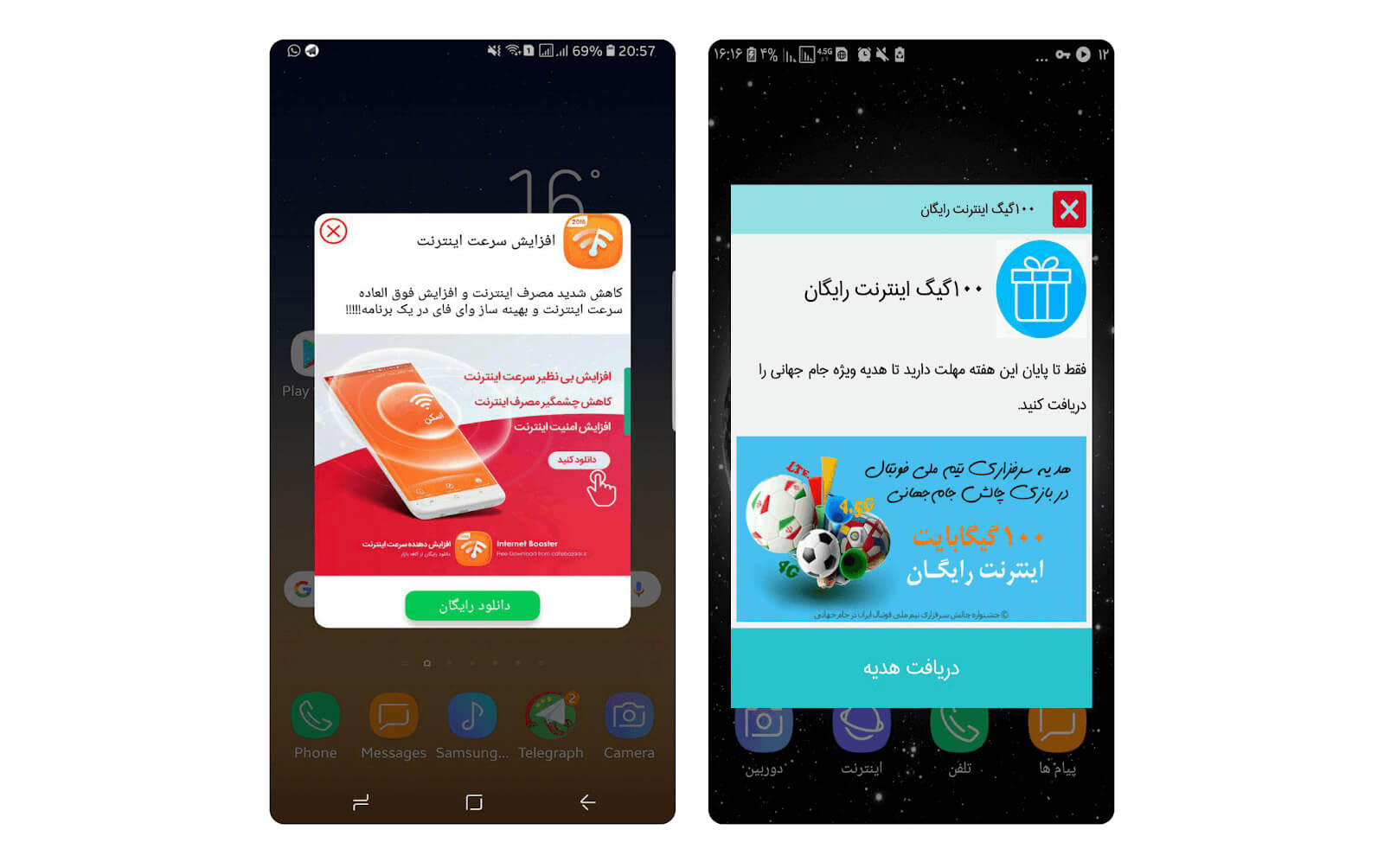
Figure 12. Annoying commercial pop-ups
6) Notification Bombardment
If a user’s device gets infected by a PushIran.DL downloader, it will gradually suggest that the user installs a number of new malicious apps. If the user installs these apps, the device will be bombarded by notifications for several hours throughout the day.
Figure 13 demonstrates some of these notifications.
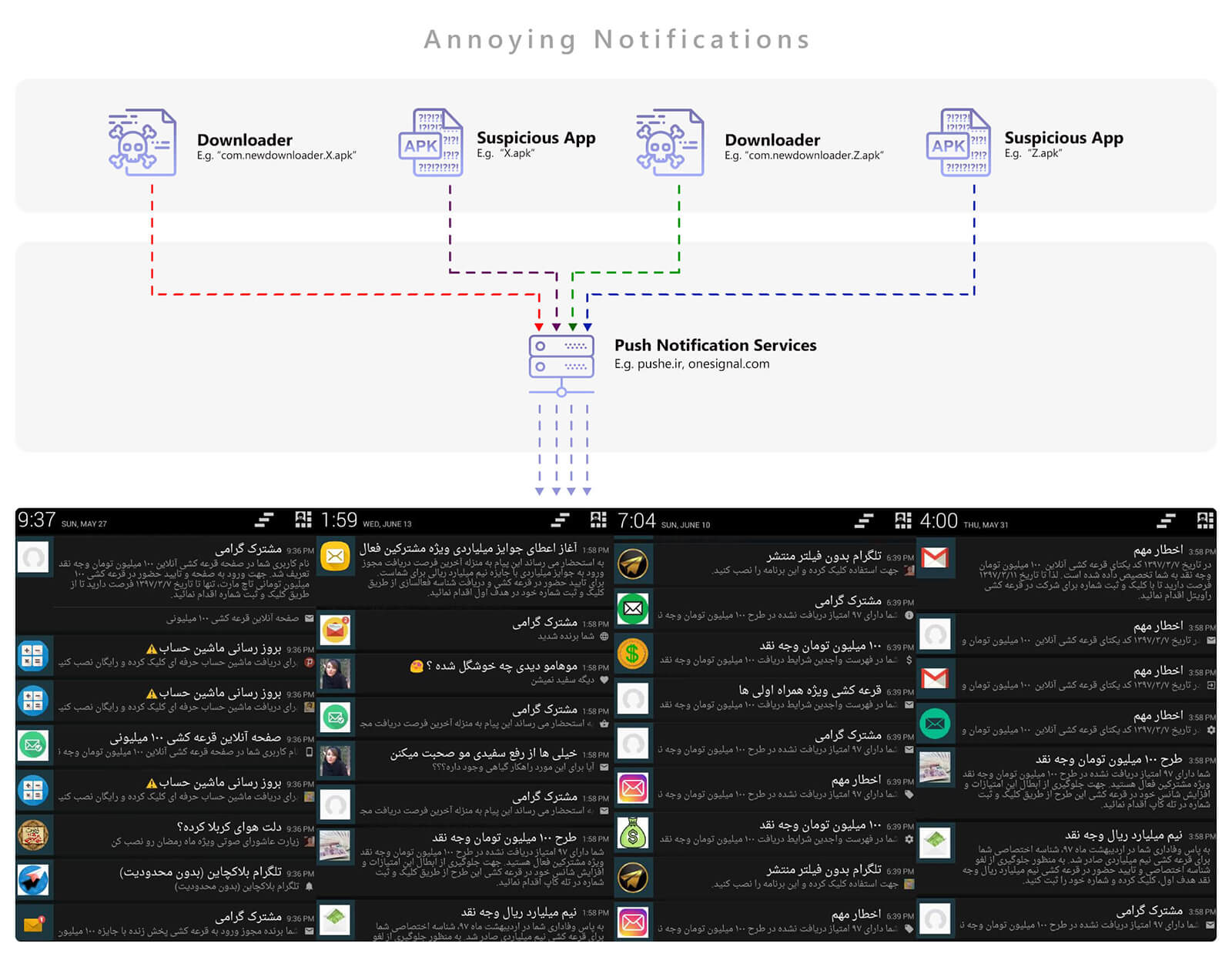
Figure 13. Annoying commercial notifications, related to PushIran.DL infected softwares
7) Phishing Notifications
After spending approximately two months evaluating PushIran.DL apps, we have not detected any examples where they have been used to engage in phishing attacks against users’ accounts on social media or elsewhere, but we believe that the distributors of PushIran.DL have the capacity to undertake such attacks if they do desired.
This research has shown that attackers are appropriating the icons of well-known apps to deceive users, send them fake messages, and direct them to various phishing pages. Figure 14 shows an example that PushIran.DL developers have misused Gmail’s icon in their notifications.

Figure 14. Misusing other apps icons such as Gmail
The Prevalence of Push Notification Services
Push notifications and the service providers of this feature are currently one of the main modes of interaction between mobile app developers and users. Due to a lack of monitoring and regulation of the use of push notifications by providers, this service has at times turned into a serious nuisance for users. Attackers frequently misuse push notification services as a means of remotely coordinating malware.
Services such as Pushe.ir/Pushe.co, OneSignal.com, Adad.ir, and Magnetaddservices.com (among others), are currently some of the services with the largest user bases among Iranian developers.
According to information published by Rotbenegar 12 pushe.ir—a push notification service—ranks as the sixth-most visited website in Iran based on internet traffic. In past months, antivirus services have become more responsive to the distribution of malware and adware by this website, and on occasions have offered security alerts to users attempting to access it. 13 We believe if this trend of abusing sites like pushe.ir continues, it should be expected that antivirus and online security software will blacklist this site in the medium-to-long term.
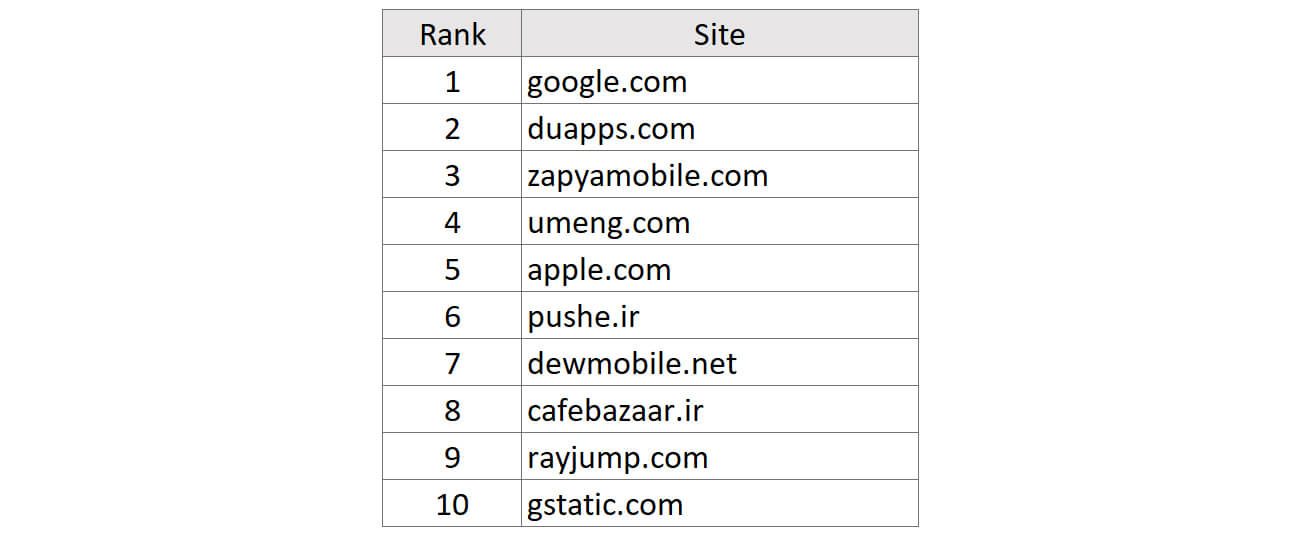
Figure 15. List of most visited websites based on internet traffic in Iran
PushIran.DL Communication Network
In order to provide comprehensive information on the distributors of the PushIran.DL malware family and the structure of this commercial botnet, details of the communications and background activity of some of the malware should be assessed. Our investigation illustrates that a number of individuals and companies are connected to each other, and use their networks to accelerate the distribution and spread of PushIran.DL.
We have also seen through our investigations that these malware developers collaborate with each other by using shared private servers to host and distribute malicious files, transferring ownership of these servers to PushIran.DL-linked individuals, and by using similar coding patterns to develop malware and push notification services.
Also, based on the information we have gleaned about the connections between servers, and the analysis of distributed malware files, we can say that the developers of these malware were also directly in connection with servers of the company Peykasa 14 for a limited period of time. This connection is, however, currently suspended.
Additionally, we identified two other items of malware (ir.pushiran.hamrahdownloader5 and ir.vira_tel.dawnloader61) which were developed by two different developers that had used tci-test.peykasa.ir and tci-srv.peykasa.ir. These domains belong to Peykasa.ir and provide a VAS to MCI.
Figure 16 shows parts of the general communication of these malware on cyberspace.
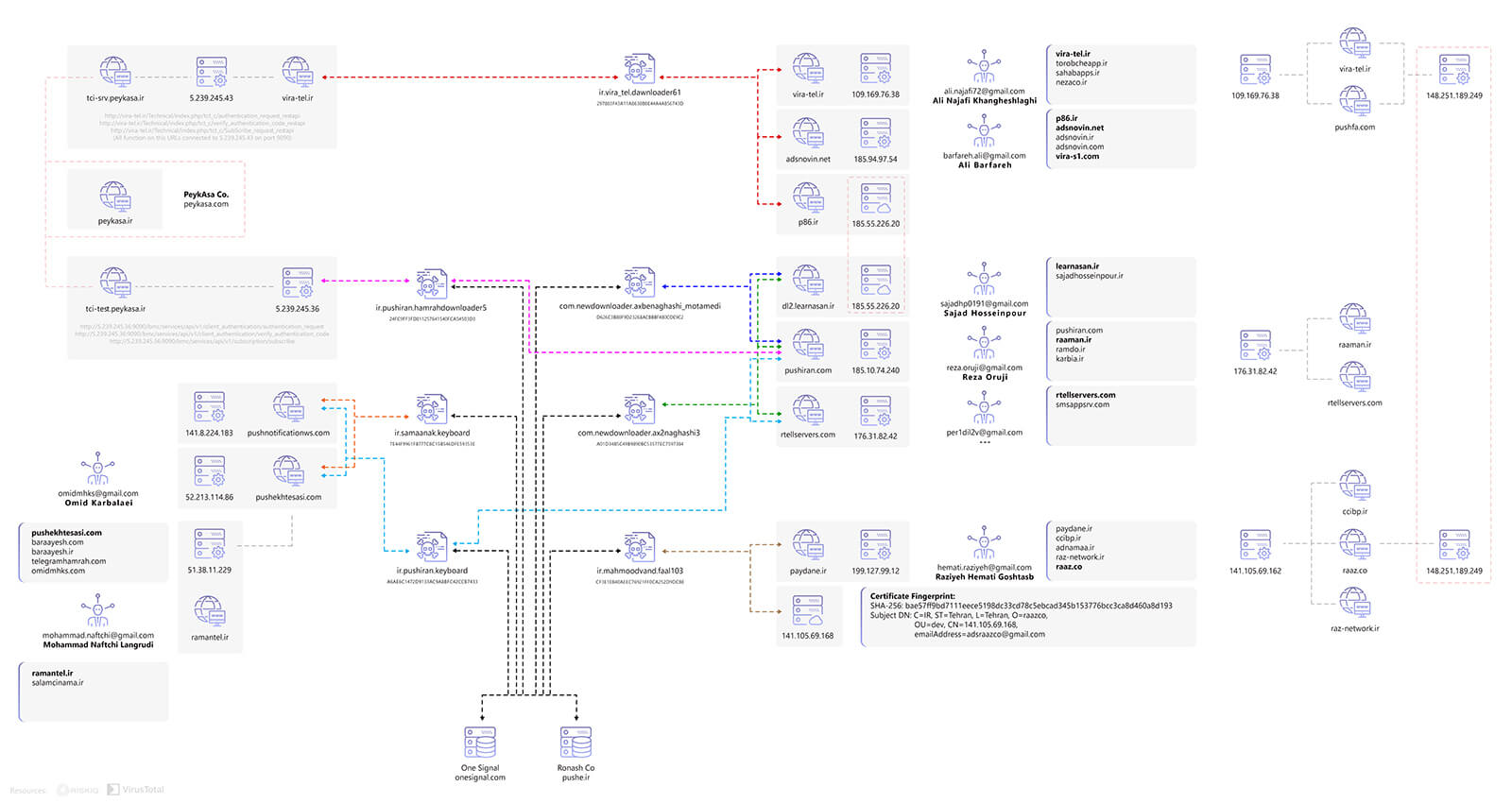
Figure 16. The structure of communication network of some of PushIran.DL malware 15
Conclusion
Although PushIran.DL is not a particularly sophisticated advertising botnet, it is a dangerous malware that has cost Iranian citizens millions of dollars. In addition, PushIran.DL allows cyber criminals (and potentially the Iranian government and intelligence services) to undertake large-scale surveillance operations. In the past, it has been suggested that state intelligence services have collaborated with known hackers to target particular individuals. 16
As a consequence, we propose a series of recommendations to tech companies, policymakers, civil society actors and internet users to mitigate the risks posed by the PushIran.DL family of malware.
Our recommendations to tech companies and policy makers:
- Put pressure on app stores such as Cafe Bazaar and Google Play to take down the malicious apps as soon as possible. A concerted effort will be required on this front, as app stores are frequently either unresponsive or slow to react to such takedown requests.
- Ensure that sure all anti-virus software is updated to identify PushIran.DL and similar malware. Currently, only a handful of anti-virus tools such as Kaspersky and Avira identify PushIran.DL apps as malicious.
Our recommendation to civil society and the Iranian diaspora media:
- Raise awareness among Iranians through different channels such as TV, radio, websites, and social media. Many victims of these attacks do not understand the impact or risks of the malware, and in some cases do not even realise that their phone is infected.
Our recommendations to users:
- Do not download any apps from unofficial app stores. Users should take time to read reviews and app descriptions before downloading any apps.
- Ensure that anti-virus software is installed on their devices, and kept up-to-date.
- Monitor all device notifications and ensure that they are legitimate. Unexpected or suspicious notifications should not be engaged with.
IOCs
- hxxp[:]//dl2.learnasan[.]ir
- hxxp[:]//pushiran[.]com
- hxxp[:]//rtellservers[.]com
- hxxp[:]//p86[.]ir
- hxxp[:]//adsnovin[.]net
- hxxp[:]//adsnovin[.]ir
- hxxp[:]//adsnovin[.]com
- hxxp[:]//vira-s1[.]com
- hxxp[:]//vira-tel[.]ir
- hxxp[:]//paydane[.]ir
- hxxp[:]//ccibp[.]ir
- hxxp[:]//adnamaa[.]ir
- hxxp[:]//raz-network[.]ir
- hxxp[:]//raaz[.]co
- hxxp[:]//pushekhtesasi[.]com
- hxxp[:]//pushnotificationws[.]com
- hxxp[:]//vira-tel[.]ir
- hxxp[:]//pushfa[.]com
- 141.8.224[.]183
- 52.213.114[.]86
- 51.38.11[.]229
- 141.105.69[.]168
- 199.127.99[.]12
- 141.105.69[.]162
- 148.251.189[.]249
- 176.31.82[.]42
- 185.55.226[.]20
- 185.94.97[.]54
- 109.169.76[.]38
- 97EDEDDB68FFCDB658FA5C62DDCCD47B
- 63FCC338838D74BB7DF69DB3A1257E95
- 7C64277C3789F8643A23C6F2DE1265CC
- FC754F72EC99561C17446F3FE61EF88D
- 3B21A8984E47325A7274C823F9E15795
- 1DF44C6A6452668C0813671BB6170C83
- 3084499EB2259869CEF1898323B4633C
- 546FE5F8227E7CFE31EB5A0A8D39A4C3
- DA944852A61C595D95F794BC9FFD1946
- E4D53B9B0998B48C35231C4020683524
- D7A2AEDE1ED47A934DED3DB62775794D
- 59C0422DA7D0776E10B45F7A7E20CD36
- 9889968AE891F7C9E054E09276C57C1C
- 361FAB76D83605361742E6B58D50F560
- 18C23582652139FF07CAAE7764E9DA31
- 18169A5CC491B295AE5AC61A303FC459
- FE900050BFF44040CA509B32C6E10C3E
- 76053A8C9B4EE2AB1C41B754A3862347
- 5F4B7F3DCE45A7A44B07A7AEA58F80AC
- 18D8130484F071632694C523FA0F9A90
- 1D769A0E6A4562CB7D078D7DD2B03723
- 3C66581D947399CA5F2365DD357F0DF1
- 29FDED3CC6092C916934978D18CF10EE
- CC9D85DFD31428C81B24C4AAA01DB6EC
- 80851BB4F58737E384151E574C8305AC
- EE2B09F987236E7D5050102852B9FFED
- 108F3F5D48B8662AE819629AFAD96DD6
- 62E55A956D22CE58515DE7AF4B1F0A01
- 59DBA392C3E8481B4937A0B0F6DD03A0
- 5DE49A12C99784915D1C5AEFD15F0689
- 3BB95502918695657F05821490CB8FBF
- 6507B6D3EDEDE67CD7C3602679D99AC2
- 6F024D50B157795D75D7B4F4833D8D73
- C7E2FD751B1D12807A7EE5C885A68FE2
- 9CD9F1B0477874C167B70423E9EFF58B
- 3676D0A702CF6E93978E3C098CCE81E3
- 297883F43A11A8638B8E44A4A856743D
- 5D89B9F1E1EABB7D17B8B0E73A13C189
- 3EC866A67CF5E595AC57BC77A35D31E5
- C48F824ED91A9EACD10B1C60C133C8EE
- 0877FD18E41B95157A177F95748985D3
- 07B228D60FC49761FF0F688986D005B0
- 09FCA078BD4FF21450F1467A939E13E2
- 7E5F627965A898ABBA918A1AD4F04997
- ADD2082A07BA09E233AB7729697F3BE9
- 04D887224BC3265CC7FE941FC7AE5CA7
- 0FA4456FFFA252BAB687422801149260
- 8130551AA4272472CD4D2176F8D9DC3A
- 00455ECD8906AE32CFCB21C0970B06FC
- 3757A65A4A495788FCB55A17673D4E7D
- 711848DBAA268A7E3C0266BC89CF2732
- A0AE93B3EF88F53165CC3DE8EF9FDDBB
- C9A528F2F1CB57B1E9453A70038487C4
- DCDE4F634CF96192ED559B53B4030524
- 7D8684F8EDA27E12E53F891C429BC16E
- 819071C1946E44F0150A95A99053A73B
- 9C13ADE8D2A32A9341FE24429A2E82DD
- 2F87B2E5E0BE432E4F8B8A95C968BFFA
- 79806218963F1FE3697C4C2FB898F1C2
- 357379FC06DA3A4C97CDD10FB5B17F41
- 3B4FCBA6EA1C13C6B53DB74F3E52CD86
- A045C341E46F8CC45E2D52F6C45D7ECE
- 8A61B42E6C8B76DF856D61325EF342FF
- 15D6ABB9D883773DDFBE470CB97AF070
- B2821BE51DB20CDD225B392B60264358
- FD8B62C5D21564A1F7B9E0B322CE027A
- 34362890337346596EA27A1C60BAA15D
- F17183E5786C4764F444B9FBD683FAB9
- D626C3B88F9D23268ACBBBF480CDE9C2
- 33C52133CB754A8CC1687C62696F6484
- A41266DB0D25C3F337E970BF4220B4EB
- 950A629D833FC267C043E57F2B418B3D
- 24FC9FF3FD811257641540FCA54503D3
- 7C73A00E4D809463A5B2A5080A18300A
- CC41F3D8DFB5C02689DEDB014AE34F1E
- AB704284032127DADCAD365AE7B09A00
- 566EA625666C852674D43BF3E9622E6D
- 5EA2A70BE79F4717926DB41E9E865577
- 7C3736B4E297497EF623FF16F39844AD
- A64128C49FCFD631DC586269FE50B2B3
- E3D2A86300AA8F0D6819EFAC894AF382
- D848C4B2925FE2A84D32BA4E02B5C54E
- 1A66FB4717345ADD364E116F7868F1FC
- AE42855522F4CF84D1E4AE07BBC71ACF
- 0507446D922636B225E9757EB7740225
- 2D794E8FA37A3F1E3A905C1FE4CF9972
- 6E5FCDAE6541748C47AE8D788B47CF01
- EB9CBBF7220E5EEDD16774D126DA84B0
- 73F129486D461305D7C28759990F09C3
- 7FC10BB84206FD034641963B371FF32A
- CF3E1EB40AEEC76921FF0CA252D9DCBE
- 199833A3C725009C21BC4EDE2545767A
- 492751DB732EDB95985E780F72C4F417
- 4D8B2B0B67A16363B1A13B00D767126A
- D86FCE725A15C62E9422A37D5877C04A
- 05539EBD4B1DE3544BC06A18287BF283
- D183E556CC7C412F57F595A0EF6323D4
- 3DB23780988F00FF8AD594F6D039624A
- ED8CC993D182C843B45B85E5F4E33F08
- C63813F981D15C2B4F3D95DFEB757916
- B4735D9F93AA5CD5B3A8BC4A555BDA2B
- 2CC3774798FF28A8D011BEE9B79AE0AD
- C9730594A846F5C168D4ECC0C438ACCB
- 1EC2936D846A6D3A2C3FF4E25D2D247D
- 96A843E6C5928421038512FF35EE4EEC
- 21C87A3227B66CB6F6DABE7B20FE48FD
- C72ABA6E5A60F940CEB8B9F04C7D9CE9
- 1E9A104ADC3632F5CBF084463DCBF0F7
- 4905BF90DF6E090C0EE3F98126FECF8C
- E4136054DBC171F1218A9C54FBA06A9B
- 75CCBD5BB01F74F3354E2D0AD84596AB
- 4B979BECAD227F38EB11D1DD40F2C368
- 4B21A4E94C7B6A684DD18CB8B7A9E5B5
- 63BCC3B576E96A7B32DA2705E16F005B
- F95079081FEE1C7930DB5336FB476661
- 54DDB4B2A30C818D91AD01CF34570C3E
- A427693D6BD83F6DA2CD8A15F44339DF
- 85DC52F4EC558A28B8C09D75C4866188
- BEF227710F9BDF2AB0D5BC8755393092
- 8170DA762292A850E378DE048A9B1458
- 5B8574D26CD5F642ABB0B7FC47E50E79
- 6435B46852BDBF0B028ECC7646D8C1C3
- 8A96B9AAE07A5B7D7232797594D64E72
- 9997568DE8F738B899F0D44AD674D1C8
- 70B069785D21527DE46358431AEBE564
- 7D9DD118AA9D8B3DEC31C104438DA959
- 04B2A0FB8350AF0E367829441291F5B3
- A5419DFF5FA4E454BEF5C6DB0B54F7D7
- 7388B6771E5A4472D7EF365627F48AAA
- 9D05A3D8F906F0DDA4E51602F7C6F19C
- 990FD5D3DBCB96DA40885E795592AFAE
- 81B73BC100361702222313686D7B867C
- 607322960E238ED7012E291DEFF06044
- 671300D228F1F5783805E4E11A6583E8
- 21A2BF1488C6E573DD6C925DA04CD826
- 112B2DE466BCFCB1EA4FF60EBA96E8EC
- DE58F4AC23E20812B8A6BFE95EB3F87E
- A9900818146E1905AED6EC4E4BAA6FF4
- 7F2AFC17AB5C2D9C73203CB275524EA6
- B389A3346BE44A94751226995FA57AEF
- A4FEEC80651C38F044C5212FD25E7015
- 98DE5A776DC4B24841EF870DADA3E5A8
- 45B2C9BCBBB4D4355ADC0579BA96E62A
- 10E2172C2FF8DF4F45CF72577D53489A
- DA16E98E26F49B7905E417F22B84573F
- D87A3BDAD1BCCC6693B5D15509F5753E
- C27275F27B7BD16836F647A5222463EC
- 60B2B3B8D47C2060CBBFB2B242634F31
- 127F3EB9E465DEF9A881B39254D305CC
- DCD2CDC4868DB9600BD6BE120742D101
- 3A1C2547A4681BFE447513357DA95995
- 3E13CC6B144247DCA5AD19D1FB66927B
- 33AE99DC1B44362397FCF5BB03D6F6C8
- 5C681DDA1C83F2BC69B6243B446CD7C7
- 582DB6FFF5AF363744EE4F0A0283F4F4
- 95A6D21589F9E1F0AFC6AE620363239E
- DDF720428B1559D19AAC245443F0E860
- A01D34B5C49B9890BC53577EC7597384
- C2B3666FFF5427D6C728AACF23A35A36
- BB8D2457077AF4CA6607FC7E5C56C806
- F66F133434266EC740570A3AF94F3C24
- BF10CFA7F8CF3C2D44C138AD0938BBA7
- A3AC33C3C07ED71844E3283735055470
- 2FE54067FE8440C5F735661B3D3A26A1
- A8A2DD036FC99E4406BDD52C6E2AFC2B
- 389051826AF93E382F639AC456C081DE
- 9B0435FC04689A1564D5FABAFA7D9FC5
- 148E7B7B94E317F4A7872BA3895DEBD3
- A0143FAC861D905DAAA004444840F4E7
- 89B197AE0F474837343BED55CAA078D9
- 2E9FA8980B2C2413C32D2D7B99329BBA
- 4D1DF6179570CE3A2C8B6DE9D29FF052
- EADEBCEE5635B9F7DC8BA18753A338D0
- 9C8230ADFFD2192D04B65A20F8A83B1D
- 89EE2394E135522C89439EEC5071FA1F
- DE55823D0CF249B0B4CC43A2E9618FC7
- AF93809C505D95D1AEF166F645DC0A14
- 603DC11FF3BB9315033858ECAE8554BF
- D2E9162ED98E62E3279936506C21461C
- DEA0CB1052D9E8CFB9FF023E35369E0A
- A2F1AACEEF10FEF6D80D1B3E3D44FCC6
- 100C846EE07428A3E0A12DA75A285116
- DA56FB59B5AB3D2A41CDFAC6D8898585
- C366A0A99C1A2AFFE38194E30CF25C26
- E854D0E5A7F7B9FAA47C0F36B261DCA7
- A38452254CA750154E402804A41ACD5B
- 63503A0886D06F728AB6B74C93BA4481
- 83493EE9FD85AC46E0FD93FCE8AD4DD1
- BB9042D360084A175E4718C50066DEF5
- AC74BF3DEF39B8F8D9234665631620F9
- 5ACA3B824A2D43179903C90C37072A42
- DDE46695E72F7654B695E4EF929DD556
- 7B5A230D549E3CE64655D0EEFBA72459
- EC6CEDD89229648CC0319CE6B8712664
- FBE5353F17F05854242E73EEC7D2AC1C
- 54EA86FC2E5F0787DE4AF478AB2E5504
- 1623DFA5C5D9786359974D359D7C9D8E
- 6369A81D283BEA485D57768C4190048A
- 0BF8E07C62CCC5C06C5ECA3F40E5C350
- CB35C962AE76B5C825761F5621FFA33F
- 5EC257CEF919237E6079247F59C09727
- 3BFFA1C45E9C8918FE7EFD9F5A900A1F
- 3AE443BA02264D546E39558F76A6FFCA
- A5B81672F5BE5AEAA98F03FCDFF58FC0
- BABE31C7B97D67A2D10B26C8FB0B90EF
- BC43EBA23B72928FA1BEF700BBB673B6
- 6F3E01C3CF32BF3161D6F00EBC605119
- 11D4939B518CC6847903181298FEAF3E
- 96CD61A12D303C2ED2F90FD61F448736
- 833181700A843509463D70294530FBF5
- 5FB4B394F619A405878E5F9DEB91F7E5
- 701E838387470E269FFA46A0CBC5EE9B
- 92EDC588244FAB6591C34985141D335B
- D004D6061A71B371E06FD35614DD623C
- E60ABFBA937606CB0FAB6D8223698886
- 7E44F9961FB777C8C15B546DFE59353E
- 78905C41D0C2BE1638AF42DE27B4EBC7
- 137C774F594931875EF5128ED1F22B61
- 6997E643AAC72B6B5FC6C67E164F6780
- 5981A50EFEEBC3C18C60E6DBB7E98650
Footnotes:
-
Command and Control servers are the central computers that are responsible for issuing directives to devices that have been previously infected with malware, and coordinating botnets. ↩︎
-
TSP stands for Telecommunications Service Provider. ↩︎
-
VirusTotal, “ir.byd.fastdiviceandro”. Accessed July 18, 2018. https://s.certfa.com/dFos6X
VirusTotal, “com.sm.antivirus”. Accessed July 18, 2018. https://s.certfa.com/pUI2hj
VirusTotal, “ir.vira_tel.dawnloader61”. Accessed July 18, 2018. https://s.certfa.com/HmHvm9
VirusTotal, “com.am.speed”. Accessed July 18, 2018. https://s.certfa.com/WpYT8q
VirusTotal, “ir.mf.antivirusm”. Accessed July 18, 2018. https://s.certfa.com/TKsFzc ↩︎ -
Pouya Ertebat Raman’s website. Accessed July 30, 2018. http://raaman.ir/ ↩︎
-
Raazgostaran Andisheh Fartak’s website. Accessed July 30, 2018. http://raaz.co/ ↩︎
-
Rooznameh Rasmi Keshvar (2017), Pooyan Ertebar Raman’s details. Accessed July 18, 2018. https://s.certfa.com/w7ekfs & https://s.certfa.com/wTm3wp & https://s.certfa.com/rI9a7W ↩︎
-
Rooznameh Rasmi Keshvar (2017), Raazgostaran Andisheh Fartak’s details. Accessed July 30, 2018. https://s.certfa.com/vZpSpW ↩︎
-
Google Play, “آریاگرام ضد فیلتر و حالت روح (فوق پیشرفته)”. Accessed July 7, 2018. https://s.certfa.com/R4eeRK
Google Play, “بهینه ساز باتری هوشمند”. Accessed July 30, 2018. https://s.certfa.com/APceTq ↩︎ -
These three categories were defined as follows:
- Malicious: We identified these apps as containing malicious downloaders.
- Fake Apps: These apps did not perform the functions they claimed to, and are suspected of carrying malware.
- Suspicious: Although no malware was detected, these apps were published by the developers of other PushIran.DL apps. ↩︎ -
MCI stands for Mobile Telecommunication Company of Iran and it also known as Hamrahe Aval.
The important point about VASs and the revenue obtained from them – such as the sums listed in the above table – is that the majority of profits go to monopoly companies that have contracts with TSPs 2 and only a small portion of it will be paid out to malware developers. This has caused some dissatisfaction among the developers. For example, you can see some of the conversations among malware developers about the low levels of income from working with VAS companies in Figure 3. It is noteworthy that these individuals are aware of the criminal nature of their activities. ↩︎ -
Karbala and Ziyarat Ashura are related to the Battle of Karbala that took place on Muharram 10, in the year 61 AH of the Islamic calendar (October 10, 680 AD) in Karbala, which is located in Iraq. This battle is symbolic of the fight against tyranny and an important event in Shia Islam. Ziyarat Ashura is is a Shia salutatory prayer to Imam Hossein, the third Shia Imam. ↩︎
-
Rotbenegar, Ranking of top 10 websites in Iran. Accessed March 7, 2018. https://s.certfa.com/hAZRMW ↩︎
-
Pushe.co (2017), “ماجرای پوشه و آنتی ویروس!”. Accessed July 31, 2018. https://s.certfa.com/yqEPYz ↩︎
-
Peykasa’s website. Accessed July 25, 2018. http://peykasa.ir and http://peykasa.com/ ↩︎
-
The high quality of Figure 16 is available here: https://blog.certfa.com/posts/pushiran-dl-malware-family/network.jpg ↩︎
-
Deutsche Welle, https://s.certfa.com/9jN3HJ ↩︎